Proof-of-principle experimental demonstration of quantum secure imaging based on quantum key distribution
2019-11-06YiBoZhao赵义博WanLiZhang张万里DongWang王东XiaoTianSong宋萧天LiangJiangZhou周良将andChiBiaoDing丁赤飚
Yi-Bo Zhao(赵义博), Wan-Li Zhang(张万里), Dong Wang(王东), Xiao-Tian Song(宋萧天),Liang-Jiang Zhou(周良将),3,†, and Chi-Biao Ding(丁赤飚),3
1National Key Laboratory of Microwave Imaging Technology,Beijing 100190,China
2Institute of Electronics,Chinese Academy of Sciences,Beijing 100190,China
3University of Chinese Academy of Sciences,Beijing 100049,China
Keywords:quantum secure imaging(QSI),quantum key distribution(QKD),digital micro-mirror device(DMD),quantum bit error rate(QBER)
1.Introduction
How to enhance the anti-jamming ability of radar is an urgent problem to be solved in the traditional radar countermeasures technology.[1,2]In the last two decades,with the intensive research and development of the techniques of quantum communication,[3–5]quantum imaging,[6–22]and quantum radar,[23,24]a series of results have been obtained,which provide a solution for improving the anti-jamming ability of radar.
In 1995,quantum imaging was first observed,[6]also known as ghost imaging(GI).Entangled photon pairs produced by spontaneous parametric down-conversion were used,while one of the photons passing through the object was collected by a photon counter or a bucket detector with no spatial resolution(called the signal beam or object beam),its twin photon was detected by a multipixel detector[e.g.,a chargecoupled device(CCD)camera]without ever passing through the object(called the reference beam).Nevertheless,by correlating the intensities measured by the bucket detector with the intensities of each pixel in the multipixel detector,an image of the object was reconstructed.[6]In a long time,entanglement swapping was considered as the necessary condition for GI.[25]However,from 2002 GI was implemented by classical light sources,[9–18]especially the groups of Wang,[12]Wu,[13]and Han[14,15]accomplished a large numbers of GI experiments based on pseudo-thermal or real thermal light sources,which proved that entanglement is not the one and only way to achieve GI.After then,computational ghost imaging(CGI)was proposed[19]and verified by experiments,[20,21]which could be deployed with only one optical beam and one detector with no spatial resolution by replacing the reference beam with a controllable and pre-modulated light source.[22]The greatly simplified imaging system reduces the number of preset patterns and the imaging computational complexity,and then raises the imaging efficiency.[22]Based on the above,CGI and quantum secure imaging(QSI)could be applied to radar imaging faultlessly.Reference[8]introduced an anti-jamming quantum radar imaging(QRI)that utilized the BB84 protocol quantum key distribution(QKD)based on polarization encoding,which could verify the authenticity of imaging information by detecting the consistency of photon polarization states between the sender and the receiver. Up to now,the BB84 protocol is the most mature and widely used quantum key distribution protocol and its theoretical security has been fully proved.[26,27]Therefore,intercept-resend attacks are exposed immediately and the authenticity of the imaging information can be guaranteed through combining the CGI and QKD on radar technology.In addition,the quantum imaging technology has many advantages of higher resolution,higher contrast,higher signal-to-noise ratio(SNR),and less influence of atmospheric turbulence[7]compared with the traditional imaging.QSI will has great application value in the fields of aerial detection,military reconnaissance,and battlefield imaging in the future.
Inspired by Ref.[8],we present a QSI scheme combining the phase-encoding BB84 QKD and CGI technology.Unlike the original scheme,our scheme adopt phase-encoding QKD,in which the relative phase is rather stable against disturbance.Moreover,owing to the fact that perfect single-photon source is still unavailable,a pulsed laser source with Poisson distribution is used in the QKD system.By combing the decoy-state method,we can estimate the contribution of the multi-photon part to obtain the lower bound of QBER under the interceptresend jamming attack,which is tighter than the origin one.In our experiment,a digital micro-mirror device(DMD)with quick response speed is used to preset the specific spatial distribution of the light intensity,and a single-photon detector(SPD)with quick response speed is used to measure the total light intensity,eventually the image of the object is retrieved through calculating the intensity distribution and the total intensity of light.Comparing with the traditional ghost imaging(TGI),QSI has been greatly improved in the data sampling rate and reduced in the imaging algorithm complexity and shortened the imaging time.More importantly,the quantum bit error rate(QBER)and the secure key rate of QKD are obtained in the experiment to see through the intercept-resend jamming attacks and ensure the authenticity of the imaging information.
2.Theory and method
The QSI system contains the imaging system and the QKD system,as shown in Fig.1,which mainly includes a QKD sender(Alice),a QKD receiver(Bob),and the spatial light path of CGI in more details.In our scheme,Alice sends out strongly attenuated coherent states with key bits information,which is encoded into the relative phase of a pair of coherent states shifted in time that are generated by an asymmetric interferometer.These photons pass through the beam expanding lens,the obtained speckle is then modulated into a specific spatial distribution of intensity with a DMD.The pulse with certain intensity distribution illuminates the object,and is coupled into the receiver,performs the decoding and detecting procedure.Finally we can reconstruct the image of the object with the detected counts.It should be stressed that in the QKD procedure,the key bits information is encoded into the relative phase between the two time-bin mode of signal pulses,which is rather stable during the display time of one frame of the DMD,since the modulation of DMD just changes the global phase of the whole two-time-bin pulses rather than the relative phase between them. Therefore,the pulses passing through the imaging optical path and arrive at Bob without changing the coding information,and can be further correctly decoded by Bob.Compared with the conventional CGI system,the major difference is that the light source and detector are replaced by a QKD sender and receiver in our QSI scheme,with which the security of imaging can be promoted.As it is necessary to measure the photon counts and QBER during the display time of every pattern loaded in the DMD,the trigger signals of the laser,the DMD,and the SPDs should be synchronized.The image of the object is reconstructed through calculating the pre-modulated intensity distribution of the DMD and the measured total intensity of the SPDs,while the QBER is monitored to estimate whether the imaging process is safe and real.
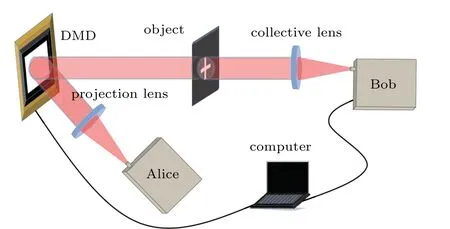
Fig.1. Schematic of the quantum secure imaging system. Polarized single-photon from Alice passes through the beam expanding lens,is modulated into specific spatial intensity distribution by the DMD,then transmits through the object,finally is coupled into Bob and detected by SPDs.The image of the object is reconstructed and the QBER is monitored to estimate whether the imaging process is safe and real. The angle of reflection from the DMD is exaggerated in the figure for clarity but is about 24◦in reality.
2.1.Quantum key distribution system
Quantum key distribution technology is one of the most mature and commonly used communication methods in quantum communication,as well as the BB84 protocol in QKD protocol,whose theoretical security has been fully proved.[26,27]So,we adopt the scheme based on the phase encoding BB84 protocol of QKD.[3,4]Our QKD system is shown in Fig.2.It is composed of two parts of Alice and Bob.Alice uses a pulsed laser to produce coherent pulses.An intensity modulator is used to produce signal and decoy pulses of differing intensities.The vacuum pulse is produced by omitting trigger signal to the laser.An unbalanced Mach–Zehnder interferometer(UMZI)with a phase modulator(PM)in the long arm plays the role of encoder,while there is an identical UMZI in Bob.[3]SPDs are deployed by Bob to detect the interferometric outcomes from the interferometer.Moreover,an electronic variable optical attenuator(EVOA)is used to attenuate the intensity of the laser pulses to the single-photon level before sending out from the sender.[26]In the experiment,the intensities of the signal and decoy pulses are set asµand ν to perform the weak+vacuum decoy-state BB84 QKD protocol.[28]

Fig.2.Schematic of the phase encoding and weak+vacuum decoy-state BB84 protocol QKD.IM:intensity modulator;BS:beam splitter;PM:phase modulator;EVOA:electronic variable optical attenuator;SPD:single-photon detector.The signal and decoy pulses are produced by IM.Two identical UMZIs in Alice and Bob play roles of encoder.An EVOA is used to attenuate the intensity of the laser pulses to the singlephoton level.
According to the phase encoding BB84 protocol,the relative phase on Alice is selected randomly from four values 0,π/2,π,and 3π/2,where 0,π are in the Z basis,and π/2,π/2 are in the X basis.Bob measures the incoming quantum states from Alice also in Z or X basis randomly.Whenever Alice and Bob use the same basis,the two SPDs will get correct results with a small QBER.However,when they use different bases,the two SPDs will get an uncertain result together.Alice then reveals only whether or not the state in which she encoded that qubit is compatible with the basis announced by Bob.If the state is compatible,they keep the bit;if not,they disregard it.In this way,fifty percent of the bit string is discarded.This shorter key obtained after basis reconciliation is called the sifted key.
2.2.Intercept-resend eavesdropping strategy
In the practical QKD system,Alice uses the weak coherent source(WCS)together with the decoy-state method to substitute the unavailable single-photon source. The photon number of each pulse follows the Poisson distribution. The probability of finding an n-photon state in a pulse is given bywhereµis the mean photon number.With the phases randomization,the states sent by Alice are described by
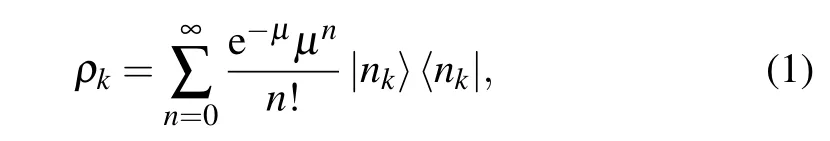
In the case of quantum secure imaging or quantum radar,the potential attacker usually adopts the intercept-resend strategy to forge the target.Since the QKD system is applied to enhance its security,here we just consider the intercept-resend quantum eavesdropping strategy that was proposed by Curty et al.[29]Eve’s attack strategy can be decomposed into three steps. In the first step,Eve obtains the total photon number n of each pulse sent by Alice via a quantum non-demolition(QND)measurement without introducing any errors. Then she performs a filter operation on the statewith the intention to make them distinguishable with some finite probability.Finally,in the third step,Eve measures each filtered state with the so-called square-root measurement(SRM).This measurement gives her the minimum value of the error probability when distinguishing symmetric states.After deciding which state was used by Alice,Eve needs to prepare a new signal in the state identified and gives it to Bob. The error rate introduced by Eve with this eavesdropping strategy for a signal state containing n photons is given by
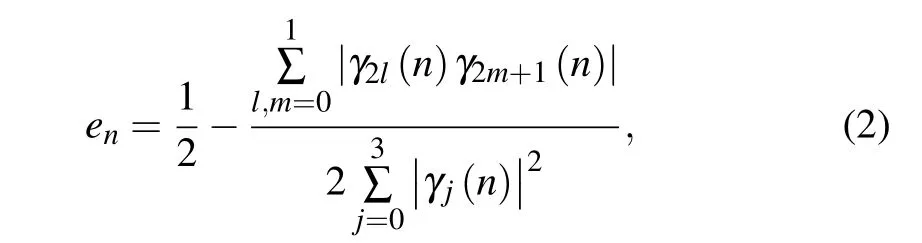




The analysis for the case of n=2 is similar.The coefficients cj(2)of the signal statesare of the formsandrespectively.The partial error rate e2is given by
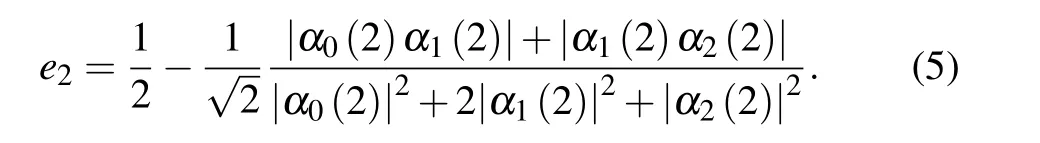
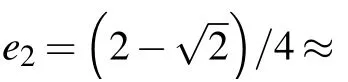
In order to give the lower bound of total error rate of the signal state at the present of intercept-resend attack,we adopt the model of decoy-state method to estimate the yield of photon pulses.[28]In the weak+vacuum decoy-state method,Alice randomly prepares the signal,decoy,and vacuum state with intensities ofµ,ν,and 0,respectively.For 0<ν<µ≤1,the following inequalities hold for all n ≥3:
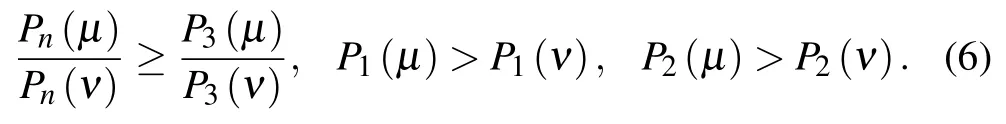
The overall gains of the signal and decoy state are given by
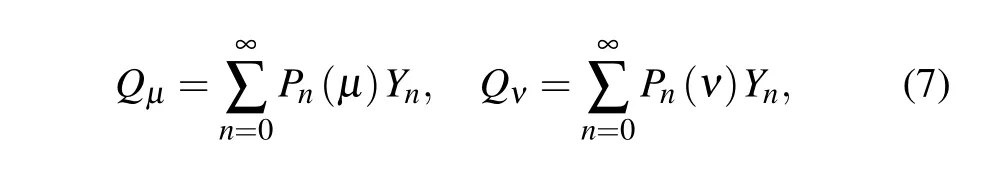
where Ynis the yield of an n-photon state,i.e.,the conditional probability of a detection event at Bob’s side given that Alice sends out an i-photon state.
By using the inequalities(6)and Eq.(8),the joint contribution of one-photon and two-photon components can be deduced as follows:
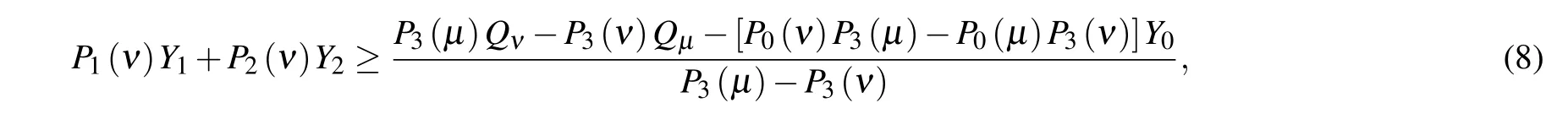
where Y0is the background rate,which includes the detector dark count and other background contributions such as the stray light from timing pulses.
The total error rate of the decoy state when Eve performs the intercept-resend attack is given by

where eiis the error rate of the i-photon state,and the error rate of the background e0=1/2.Thus we can obtain the lower bound of the decoy state total error rate
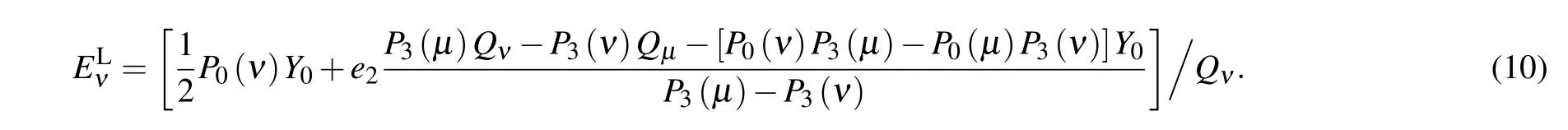
Therefore,one can monitor the error rate of the decoy state,when the error rate of our QSI system is greater thanit implies the existence of Eve and the images obtained from a signal cannot be considered secure.In addition,whether our QKD system obtains secure keys can also be a criterion of secure imaging.
2.3.Computational quantum imaging system
CGI is an improvement from TGI.A spatial light modulator(SLM)or a CCD is used to preset the specific spatial distribution of the light intensity.Disregarding the reference beam,so just a single-pixel detector is needed.[20]In this imaging scheme,take the DMD to be a part of Alice. According to the security requirement of the decoy state BB84 protocol,the intensity of the laser pulses has to be lowered to the singlephoton level at the exit of the DMD by an EVOA.
As in our scheme,a DMD is used to preset intensity patterns of speckles,and single-photon detectors are employed to measure the counts corresponding to each pattern. Suppose N is the number of intensity patterns modulated by the DMD,one can obtain the total count Bi(1 ≤i ≤N)during the display time of the i-th pattern,whose intensity distribution is denoted by Ii(x,y)(1 ≤i ≤N).Then the image of the object can be obtained by summing the calculated intensities Iiwith the appropriate weights Bi[20]
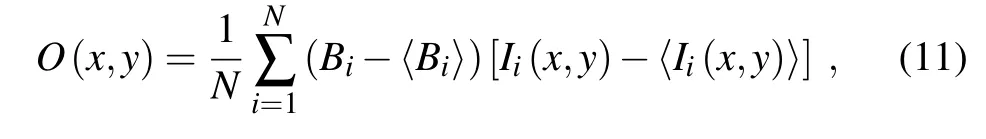
where
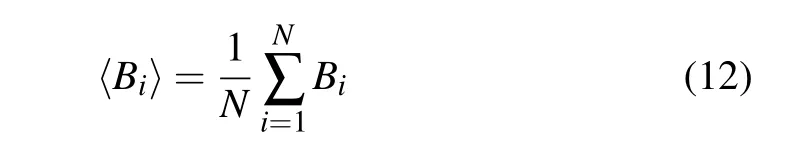
is the mean value of Bi,and Bimeets the following formula:

where T(x,y)is the transmission function of the object.
3.Experiment and results
The QSI system is set up as shown in Fig.3.In the QKD system,the pulsed laser is working at a frequency of 40 MHz and a central wavelength of 1550.12 nm.The SPD is working at Geiger mode and has a detection efficiency of 10%for photons.The intensities of the signal,decoy,and vacuum state are set toµ=0.68,ν=0.18,and 0 with the probabilities of 13/16,2/16,and 1/16,respectively.In the quantum imaging part,the array of the DMD micro-mirrors(G4100 from TI,the control board is made by x-digit)is 1024×768,and the size of every micro-mirror(one pixel)is 13.68µm×13.68µm.Since each micro-mirror is so small that the laser energy reflected from it is extremely low,a new array of 24×24 pixels is reselected and controlled with the same state in any case.The size of the new block is approximately 328.32µm×328.32µm when ignoring the gaps between the micro-mirrors.We choose only the square areas wherever covered by the light spot and the intensity is adequate enough.So,the DMD is divided into 20×20=400 blocks,Figure 4 shows the simplest binary pattern loaded into the DMD that only one block is in the“on”state and the others are in the“off”state. In all the binary patterns,each block appears just only once,which is similar to spot scanning. In this way,only 400 binary patterns are needed,which can reduce the complexity of the imaging algorithm and greatly save the imaging time.
After completing the connection of experimental devices as shown in Fig.3,set up the frames number N=400 and frame frequency f=200 Hz.Run the DMD in the fully open mode,and make the QKD work normally through scanning,and set up every parameter within QKD before placing the object.Then,put the“+”type object into this system,and load 400 random binary patterns into the DMD.Run the whole system synchronously.The signal photon counts and QBER are measured during the display time of each pattern frame.The corresponding results of the QKD procedure are shown in Table 1,which are obtained by following the standard decoystate BB84 QKD protocol.According to Eq.(11),the reconstructed image of the object is shown in Fig.5.The SNR is 23 dB,where SNR is defined asis the average of the signal intensity,and σnis the variance of the background intensity. The difference between the average intensities of the bright and dark regions of the images is regarded as the signal,and the variation of dark background is considered as the noise.[22,30]The lower bound of the error rate is calculated to be 14.51%according to Eq.(10),and a secure key rate of 571.0 bps is achieved during the imaging period.
As can be seen from Table 1 and Fig.5,the image information of the object can be obtained by using the QSI scheme,and the average QBER is 3.99%,which is below the lower bound and proves that the imaging process is safe and real.Once the jammer of object tries to carry out the interceptresend strategy,it is bound to lead to the over threshold increase of QBER under the premise of presence of photon counts. In general,we think that the jammer of object has carried on the intercept-resend strategy and the imaging is no longer safe and real when the average of QBER is higher than 14.51%.Therefore,our QSI system can be used as quantum secure radar against jammers.

Fig.3.Experimental setup of the QSI system.The red arrows indicate the path of light roughly.
Fig.4.The simplest binary pattern loaded into the DMD that only one block is in the on state and the others are in the off state.

Table 1.Experimental results of QKD procedure.

Fig.5.Results of numerical simulation and QSI experiment of a“+”type object.(a)The result of numerical simulation of imaging the object according to Eq.(11).(b)The result of using the measured signal intensity distribution for imaging the object directly.(c)The result of calculating the measured signal intensity and the presetting intensity distribution for imaging the object according to Eq.(11),which is better than(b).
At the same time,we can see that the image resolution is not high.The main reason is the serious diffraction effect of the DMD.As we know,the DMD is composed of many micro mirrors,which is similar to a two-dimensional diffraction grating.It has a strong diffraction effect on monochromatic light,and becomes stronger with the increase of the wavelength,[31]which can hardly even be used for imaging in the mid-infrared band. Therefore,even if all the micro mirrors of the DMD keep in the off state,the detector will still measure much energy due to the diffraction effect,which will greatly reduce the SNR and the imaging quality. As a result,neither the new block of the binary patterns can be too small,otherwise the diffraction noise will drown out the signal energy which makes the SNR relatively low.Nor the new block can be too large,otherwise the imaging resolution will be dissatisfactory.Therefore,it is necessary to find a balanced block in the experiment that makes the imaging quality best.In our experiment,the block with size of 328.32µm×328.32µm is relatively appropriate.In addition,we can minimize the diffraction effect by the following three methods. Firstly,we can change the distribution of the diffraction spots and energy by adjusting the incident angle of light on the DMD to minimize the diffraction effect.Secondly,we can increase the distance between the DMD and the detector to reduce the diffraction effect,because the diffraction spots are distributed at some certain angles.The farther away the distance,the larger deviation of the diffraction spots,and the less stray light coupled into the detector.Finally,we can design the wavelength of the light to match the DMD to reduce the diffraction effect,but all the devices need to be matched to this wavelength,such as the DMD,the laser,and the detector of QKD,which is a troublesome and complex thing.In the future works,we will focus on the research how to reduce the diffraction effect of DMD to make the imaging quality optimal.
4.Conclusion
We propose a QSI scheme based on the phase encoding and weak+vacuum decoy-state BB84 protocol QKD that can resist the intercept-resend strategy of the jammers. The authenticity and safety of the imaging process are ensured by the theoretical unconditional security of QKD,and the QBER and the secure key rate analytical functions of QKD are used to estimate whether the jammer of object carries out the interceptresend attacks.In our experiment,we obtain a secure key rate of 571.0 bps and a secure average QBER of 3.99%,which is below the lower bound of 14.51%. In the imaging system,we synthetically use the CGI scheme,SPDs and DMD both with faster response speed that greatly improve the imaging efficiency.This scheme is suitable for both objects with transmission or reflection. Furthermore,the system uses a WCS with invisible wavelength of 1550 nm,which can realize weak-light imaging and be immune to the stray light or air turbulence.Thus,it will become a better choice for quantum secure radar against jammers.But at the same time,it is undeniable that the more obvious diffraction effect of the DMD on the longer wavelength light will reduce the imaging SNR and quality.We believe that the diffraction effect can be minimized and the imaging quality can be improved by continuously adjusting the incident angle of light on the DMD,increasing the distance between the DMD and the detector,or designing the wavelength of the light to match the DMD.
Acknowledgment
We acknowledge Xiaoming Lu,Di Jiang,and Bin Chen for fruitful discussions and software support.
猜你喜欢
杂志排行
Chinese Physics B的其它文章
- Compact finite difference schemes for the backward fractional Feynman–Kac equation with fractional substantial derivative*
- Exact solutions of a(2+1)-dimensional extended shallow water wave equation∗
- Lump-type solutions of a generalized Kadomtsev–Petviashvili equation in(3+1)-dimensions∗
- Time evolution of angular momentum coherent state derived by virtue of entangled state representation and a new binomial theorem∗
- Boundary states for entanglement robustness under dephasing and bit flip channels*
- Manipulating transition of a two-component Bose–Einstein condensate with a weak δ-shaped laser∗
