A game-theory approach against Byzantine attack in cooperative spectrum sensing
2019-01-17WuJunSongTiechengYuYueHuJing
Wu Jun Song Tiecheng Yu Yue Hu Jing
(School of Information Science and Engineering, Southeast University, Nanjing 211189, China)
Abstract:In order to solve the Byzantine attack problem in cooperative spectrum sensing, a non-cooperative game-theory approach is proposed to realize an effective Byzantine defense. First, under the framework of the proposed non-cooperative game theory, the pure Byzantine attack strategy and defense strategy in cooperative spectrum sensing are analyzed from the perspective of the Byzantine attacker and network administrator. The cost and benefit of the pure strategy on both sides are defined. Secondly, the mixed attack and defense strategy are also derived. The closed form Nash equilibrium is obtained by the Lemke-Howson algorithm. Furthermore, the impact of the benefit ratio and penalty rate on the dynamic process of the non-cooperative game is analyzed. Numerical simulation results show that the proposed game-theory approach can effectively defend against the Byzantine attack and save the defensive cost.
Key words:cooperative spectrum sensing; Byzantine attack; game theory; non-cooperative game; Nash equilibrium
Cognitive radio (CR) has become a promising technique to solve spectrum scarcity issues. Spectrum sensing unit as an essential of a CR is exploited to identify those frequency bands unused by the primary users (PU), but without causing harmful interference to the primary network. However, the individual secondary user (SU) is unable to accurately detect the primary signal due to the factors such as noise uncertainty, multipath fading, shadowing, etc. Therefore, cooperative spectrum sensing is proposed as an elegant solution to exploiting spatial diversity gain to make a more accurate decision about the PU’s status. Nevertheless, due to the open characteristics of cognitive radio networks (CRNs), security vulnerability can be exploited by different types of attacks[1]that is launched in the process of cooperative spectrum sensing, such as the primary user emulation attack (PUEA) and Byzantine attack.
PUEA, one of the most representative attack types in the aspect of PU, mimics incumbent signals in order to cause denial-of-service (DoS) attacks, especially in distributed networks. They can cooperate and transmit fake incumbent signals, thus making SUs hop from band to band and severely disrupting their operation[2]. A Byzantine attack, also called spectrum sensing data falsification (SSDF), was first proposed by Lamport et al[3]. It manifests in that the attacker sends false observations with the intention of confusing other SUs or the fusion center (FC). Their aims are to lead the FC or other users to falsely conclude whether there is an ongoing incumbent transmission or not[2]. Different from PUEA, the Byzantine attack in cooperative spectrum sensing is a typical example of SU attack.
Recently, game theory has become an important tool, which is ideal and essential in studying, modeling, and analyzing the interaction among independent, and self-interested players. Moreover, it has been extensively used in the communication field[4]. Hence, some research related to the game theory progressively permeates the security of cooperative spectrum sensing, whereas most research directions only focus on combatting PUEA[5-11]and seldom apply the game theory in addressing the Byzantine attack problem. Several methods, such as two attack-prevention mechanisms with direct and indirect punishments, and the credit weighting scheme[12], have been proposed to mitigate the adverse effects of a Byzantine attack on cooperative spectrum sensing, such as, a cooperative spectrum sensing scheme based on the evidence theory[13]and a two-stage credit threshold scheme[14]. Besides, Wang et al.[15]presented the evidential reasoning-cooperative spectrum sensing scheme in dealing with the spectrum sensing problems in the presence of a false alarm (FA) and false alarm and miss detection (FAMD) attacks (such attacks are still a Byzantine attack on essence) on CRNs. Wu et al.[16]proposed a robust data fusion scheme, named the robust weighted sequential probability ratio test, against various Byzantine attack probabilities. The comprehensive study on the recent advances in Byzantine attack and defense for cooperative spectrum sensing was also surveyed[17].
However, these Byzantine mitigation methods derive from defense or protection mechanisms, and the cost and benefit of both the attacker and defender can often be ignored. How often and when to defend against a Byzantine attack can satisfy the demand of the network security under cost management remains to be explored. Defending against the Byzantine attacker that acts in a tragic manner is relatively more complex and challenging. To tackle this challenge, in this paper, the malicious attack behavior of malicious SUs instead of PUs is our special concern. Both various Byzantine attacks and the defensive efficiency are considered by the game-theory approach, since a positive or negative defense will cause resource waste or insufficient protection when the network suffers from a Byzantine attack at different levels. A non-cooperative game with incomplete information is formulated between the attacker and the defender. Furthermore, the benefit ratio and penalty rate are designed to analyze the Nash equilibrium (NE) of the game. In addition, various attack strategies and the cost-benefit of defense are considered.
1 System Model
1.1 Network model
Consider an infrastructure-based network consisting of a PU networks and a CRN under the IEEE 802.22 network standard model. We focus on the CRN with one primary transmitter (regarded as PU in the CRN), one FC and several collaborative SUs, wherein some of them are assumed to be Byzantine attackers.
In the frame structure for the CRN with periodic spectrum, each frame consists of one sensing slot and one transmission slot.In the sensing slot, each SU individually employs local spectrum sensing techniques to detect the absence or presence of the PU. After SUs located in different sensing environments independently obtain sensing observations, each SU submits its own decision result about the PU activity to the FC. After receiving each SU’s decision, the FC concludes with a final decision in one detection whether the channel is being exploited by the PU or not and broadcasts the status to all SUs.
In the transmission slot, SUs have an opportunity to operate the channel after the channel is announced as idle by the FC. If the channel is identified as being in a busy state, SUs are forbidden to access the busy channel which is already in use, in case of harmful interference in the primary network.
1.2 Byzantine attack model
In the process of cooperative spectrum sensing, attackers may hide in a latent place against discovery, but the local sensing ability and condition of detecting primary signals are similar to reliable SUs. When all SUs are required to send their own sensing results to the FC for global decision-making, attackers accompany in a cooperative manner. Through a Byzantine attack, in which the attacker will send falsified local spectrum interference to mislead the FC, the adversary can prevent reliable SUs from using the existing white space, or lure them to accessing the channel in use and cause excessive interference to the primary network, thereby undermining the premise of CR technology.
In previous research, a prerequisite that attackers are the minority of SUs is generally emphasized. Nevertheless, the extrema malicious behaviors imposed on the network should be predictable. Therefore, we propose three levels of Byzantine attack, valid attack (VA), invalid attack (IA) and no attack (NA), as shown in Fig.1. VA denotes that the FC’s final decision is distorted by attackers. In detail, when the inactive PU occurs, attackers advertise 0 as 1, which causes the FC to believe in the presence of the PU via a specific fusion rule, e.g.,K-out-of-N. Consequently, reliable SUs are restricted to accessing the idle channel, meanwhile, attackers take advantage of the occupying channel, termed as denial SSDF (DS)[18], resulting in a false alarm. When the PU is active, attackers announce 1 as 0, thus causing harmful interference to the primary incumbent, termed as inducing SSDF (IS)[18], leading to the false alarm.
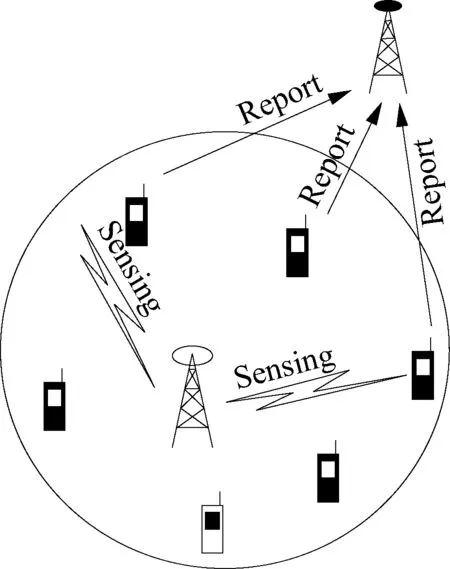
(a)

(b)Fig.1 Byzantine attack model. (a) Valid attack; (b) Invalid attack
Sometimes, attackers may be prone to carry out a milder attack IA rather than VA. The principle of such a strategic adjustment is based on whether a Byzantine attack makes the FC blind. We say that the FC is blind if attackers can make the data that the FC receives from SUs such that no information is conveyed[19]. However, given the attack cost and the attack risk, attackers do not always make the FC blind (such as, a small percentage of attackers launch a Byzantine attack but are not able to compromise the FC, which is regarded as IA, while attackers still gain the attack gain since they participate in cooperative spectrum sensing). NA means that attackers sense the primary signal as well as the reliable SUs, and are unintentionally distorting their own sensing results. As a result, they truthfully submit own sensing results to the FC.
To simplify the analysis, we assume that all SUs have the same sensing capability, where some SUs are Byzantine attackers. The following assumptions of three conditional probabilities associated with a Byzantine attack and PU activity are made: When attackers launch VA under the inactive PU, the probability of which is donated bypV; when attackers launch IA under the active PU, the probability of which is denoted bypI; when attackers implement NA, the probability under the presence of the PU ispN.
2 Game Formulation
2.1 Definition of players
There are two players, namely, the attacker and the defender. Attackers represent a set of attackers who participate in cooperative spectrum sensing. They sneak into reliable SUs and launch a Byzantine attack. As network administrators, defenders are responsible for suppressing Byzantine attacks in the network.
2.2 Attack and defense strategy
We characterizeSa={SVA,SIA,SNA} andSd={SD,SND} as the strategy set of the attacker and defender, respectively.
2.2.1 Attack strategy analysis
In the Byzantine attack model, there are three actions VA, IA and NA, which can be performed by the attacker in the process of cooperative spectrum sensing. The concrete strategies must incorporate the spectrum sensing process and the PU activity.
In order to visually represent the attack strategy of the spectrum sensing process, we assume that X-Y means the attacker selects the action X in the sensing slot and Y in the transmission slot. When VA occurs, the attack strategy corresponding to the DS results in the false alarm concerning the PU state in the sensing slot, thereby Byzantine attackers selfishly occupy the idle channel to proceed with data transmission in the transmission slot. The whole process is denoted as VA-O. Otherwise, the strategy in connection with IS can be denoted by VA-I. Due to the miss detection, all the SUs proceed with data transmission in the transmission slot, thereby causing harmful interference in the normal communication of the primary network.
The attacker launches IA while the channel is being used by the PU. The FC’s final decision is also accurate, and the attacker has to leave due to no benefits, and such a situation is denoted as IA-L. When the channel is unused, the attacker with IA can access it as well as the reliable SUs for transmitting data, which is denoted as IA-nO. After all SUs have sensed the active or inactive PU, since the attacker implements NA and operates like reliable SUs, the final decision is also idle or busy; therefore, both the attacker and reliable SUs access the unused channel or switch to another channel after the sensing slot. These two situations are respectively denoted as NA-L and NA-nO. Notably, NA-nO means no difference between the unintentional attacker and reliable SUs. Through the above analyses, the attack strategy is listed in Tab.1

Tab.1 Attack strategy
2.2.2 Defense strategy analysis
The strategy carried out by the defender is dependent on the decision result regarding the PU activity. To be specific, whether the FC broadcasts the busy or idle decision or not to SUs, the defender can select two actions: defense (D) and no defense (ND). D and ND, respectively, denotes that the defender adopts a defense mechanism or executes no defense policy. Which type of defense mechanism is implemented is of no interest, because a range of methods can be employed by the network defender. The defense strategy is listed in Tab.2.

Tab.2 Defense strategy
2.2.3 Mixed strategy
Given pure strategies for the attacker and defender, they will randomly propose a mixed strategy action in the following subsection, respectively.
2.3 Notation of cost and benefit
Before analyzing the non-cooperative game, we give some specific notations about the benefit and cost parameters of the Byzantine attack and defense strategy in the process of cooperative spectrum sensing .

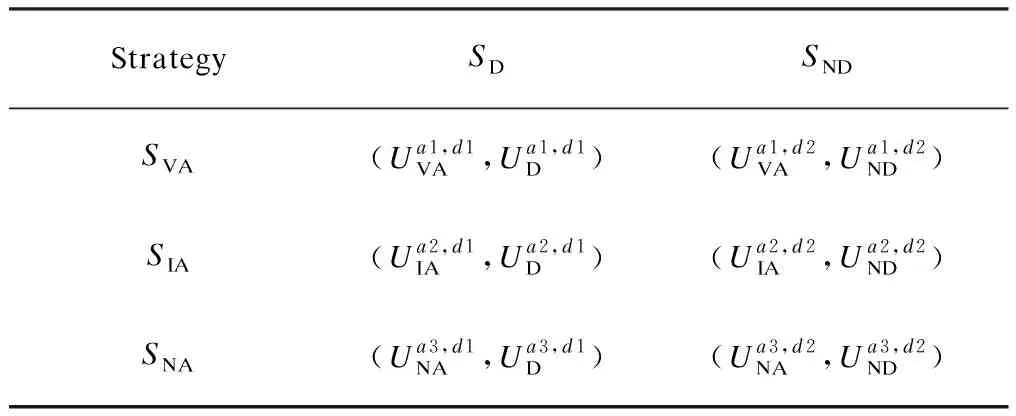
Tab.3 Payoff matrix of the Byzantine attack and the defense game
The payoff matrix of the Byzantine attack and defense game can be derived in Tab.3. According to Ref.[20], the average payoffs of the defender and the attacker are computed as follows:
(1)
Thus, by a simple mathematical investigation, the expected payoff of VA, IA and NA can be expressed as
(2)
whereσdandσnddenote the probability ofSDandSND, respectively.
Likewise, the expected payoff of D and ND can be obtained by
(3)
whereσvaandσiadenote the probability ofSVAandSIA, respectively.
3 Analysis of Equilibrium Points
In a non-cooperative game, the attacker and defender only focus on own benefit and choose the best response (BR) that can maximize the respective payoff function. Such an outcome of the non-cooperative game is termed as NE[20].
In the Byzantine attack model, given the occurrence of IA, the excessive defense is careless of the defender to evoke an expensive waste of resources, whereas the moderate defense for VA causes the network to be in a slight state of no protection. Our final purpose is to figure out how and when to select the economic and efficient defensive strategy for counteracting various Byzantine attacks in terms of the benefit and cost.
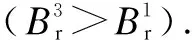
For this aim, we define two parameters from two players’ perspectives, the penalty rate and benefit ratio. The penalty rate, denoted asPr=φ/GO, makes the restrictive defense strategy unnecessary when the penalty is imposed on the attacker after being identified. The benefit ratio, denoted asBr=GD/CD, avoids unnecessary defense resource waste when the defender implements the defense mechanism unless the gain reaches a certain extent.
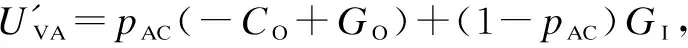
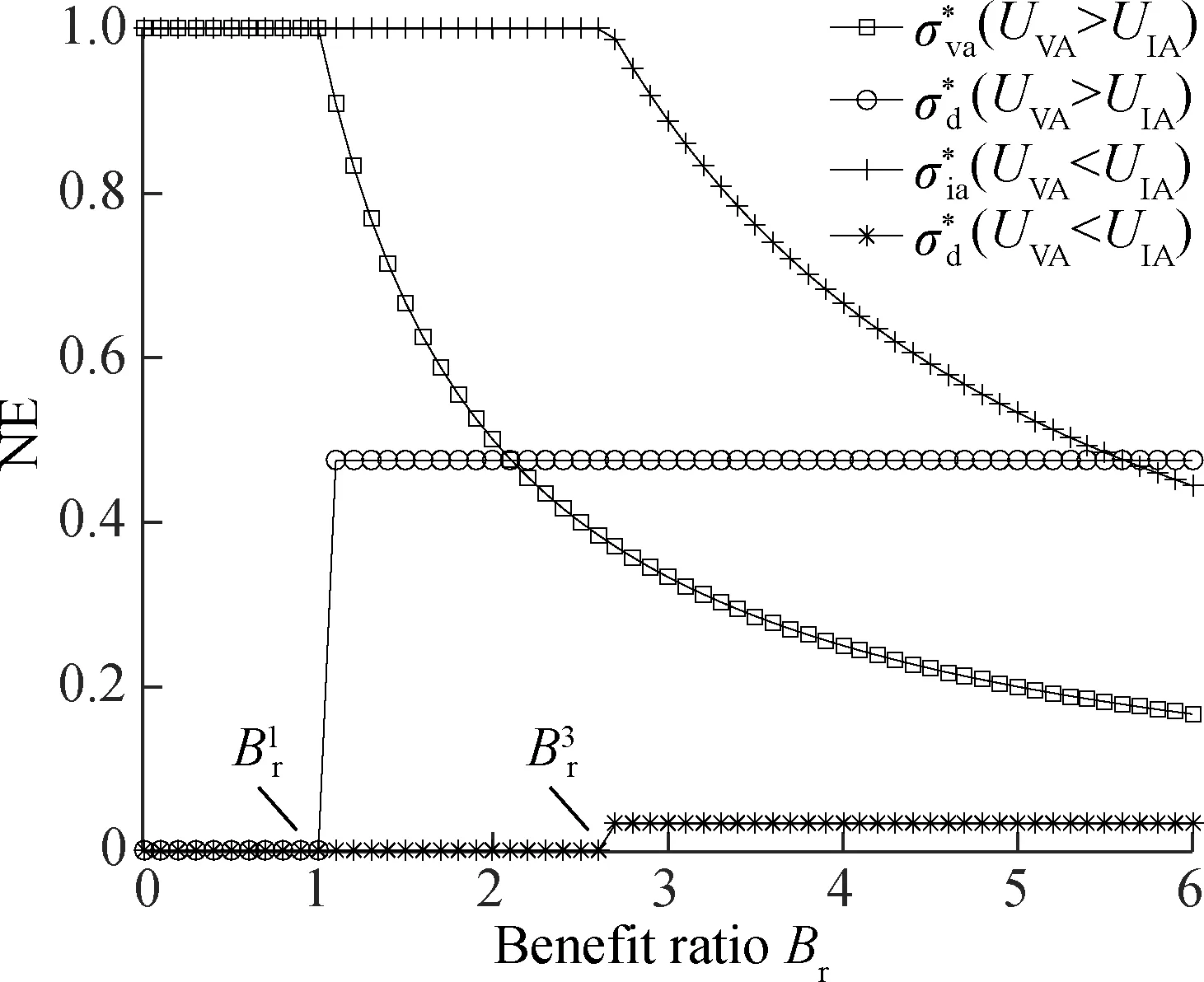
Case1UVA>UIA
ifCA Case2UVA=UIA Case3UVA ifCA In this section, numerical simulations are shown to verify the efficiency of our proposed non-cooperative game to defend against various Byzantine attacks and the impact of the benefit ratio and penalty rate on the NE. The parameters are set as follows:CA=10,pV=pI=0.25,GO=3CA,CO=0.3CA,φ=0.5CA,γ1=γ3=γ4=0.5,γ2=0.25. Without loss of generality, the above selected parameters correspond to the most significant caseCA=UVAandCA=UIA. (a) (a) (b)Fig.3 NE of the game for UVA=UIA. (a) Mixed attack strategy; (b) Mixed defense strategy It also can be seen that the defense level decreases as the penalty ratePrincreases in Fig.3(b). This is reasonable since the defender believes that sufficient penalty can frighten the attacker. In contrast, the deficiency of the attack transformation in Ref.[21] easily overprotects CRNs and wastes resources. In this paper, we formulate a non-cooperative game with incomplete information between the Byzantine attacker and defender in the process of cooperative spectrum sensing. On the basis of bilateral practical actions, the opponent strategies are analyzed in detail. We propose individual cost-benefit from two players’ perspective and derive the expected payoff over pure strategies. In addition, the closed form of the NE is obtained by the Lemke-Howson algorithm. Simulation results show that the benefit ratio and the penalty rate have a significant effect on NE, which demonstrates that the game-theory approach can take into account counteracting various Byzantine attacks and save the defensive cost.4 Simulation and Results




5 Conclusion
杂志排行
Journal of Southeast University(English Edition)的其它文章
- Failure load prediction of adhesive joints under different stressstates over the service temperature range of automobiles
- Dependent task assignment algorithm based on particle swarm optimization and simulated annealing in ad-hoc mobile cloud
- A cooperative spectrum sensing results transmission scheme with LT code based on energy efficiency priority
- An indoor positioning system for mobile target tracking based on VLC and IMU fusion
- Investigation of radiation influences on electrical parameters of 4H-SiC VDMOS
- A simplified simulation method of friction pendulum bearings
