ABORT-like detector to combat active deceptive jamming in a network of LFM radars
2017-11-20YuanZHAOZhiRANYingXIONGBinTANG
Yuan ZHAO,Zhi RAN,Ying XIONG,Bin TANG
School of Electronic Engineering,University of Electronic Science and Technology of China,Chengdu 611731,China
ABORT-like detector to combat active deceptive jamming in a network of LFM radars
Yuan ZHAO*,Zhi RAN,Ying XIONG,Bin TANG
School of Electronic Engineering,University of Electronic Science and Technology of China,Chengdu 611731,China
This paper studies an electronic counter-counter measures(ECCM)scheme combating against deceptive electronic counter measure(ECM)techniques.An adaptive detector exploiting generalized likelihood ratio test(GRLT)criterion is applied to detect the presence of deceptive jamming in fractional Fourier transform(FrFT)domain.First,the generating mechanism of spurious frequencies is analyzed based on the Volterra serial.The proposed nonlinear distortion model based on power amplifier behavior is robust in distortion analysis when the memory effect is considered.Second,a modified adaptive beamformer orthogonal rejection test(ABORT)like detector in closed form is built.The proposed detector can discriminate the echo and deceptive jamming adaptively by exploiting primary data and secondary data.This ECCM scheme is capable of guaranteeing the performance without the restriction of orthogonality,which is essential for the ABORT detectors.The expansion to radar network is discussed as a special case at the final part of this paper.Numerical simulations demonstrate the effectiveness of the proposed method.
©2017 Chinese Society of Aeronautics and Astronautics.Production and hosting by Elsevier Ltd.This is an open access article under the CC BY-NC-NDlicense(http://creativecommons.org/licenses/by-nc-nd/4.0/).
1.Introduction
Aimed at generating false targets around real target,main-lobe deceptive electronic counter measure(ECM)techniques are designed to combat against phase array radars.1This ECM scheme is often enhanced by using digital radio frequency memory(DRFM)systems.Moreover,for deceiving remote radar stations,power amplifier plays an important role in signal transmission.The high accuracy reconstruction of deceptive jamming(We note here that the notion of deceptive jamming denotes the waveform before matched filter and the notion offalse target denotes the target indication after matched filter in this paper.)affects the basic function of tracking radar systems.This makes the cancellation and discrimination offalse targets paramountly important.Thus,modern tracking radars have incorporated electronic counter-counter measures(ECCM)techniques to combat against the ECM signals.
The ECCM techniques for tracking radars can be categorized in accordance with tracking procedures.Generally,radar systems conduct target tracking by transmitting an optimal designed signal,receiving targets returns by an array of antenna,processing target detection and parameter estimation,and processing targets tracking.Moreover,the network version of radar stations applies information fusion for better targets detection,tracking and ECCM performance.Tran smitterbased techniques include pulse diversity,2,3frequency agility,and pulse repetition interval(PRI)jitter.These techniques ensure that the jammer cannot easily anticipate the radar pulses.Besides,the application of low probability of interception signals4makes it difficult for jammer to estimate the parameters of the victim radar station.Antenna-based techniques are capable of preventing jamming from entering sidelobes of radar through sidelobe blanking and sidelobe canceling.Signal processing-based techniques adaptively cancel the deceptive jamming based on the assumption that jamming signals and echoes are not overlapped in time,frequency,space or transform domains5–8after some specific processing.Furthermore,adaptive discriminations of deceptive jamming and echo based on the finger print features9and subspace structure differences are also reported.Data processing-based techniques10–12apply target tracking and reject false targets through their range,angle,velocity and acceleration under the assumption that the deceptive jamming will introduce a mismatch on motion behavior.However,the limitations of ECCM techniques are also obvious.The complex transmitting signals will increase the computation burden and may decrease detection performance.Antenna-based techniques are only feasible for sidelobe jamming suppression.Signal processing-based techniques are highly affected by signal to noise ratio(SNR)and jamming to noise ratio(JNR).In addition,when the jammer modulates the false targets accurately onboth timedelayandDopplerfrequency,thedata processing-based techniques will come to failure.Thus,a network of radar equipped with ECCM techniques can enhance the performance against deceptive jamming.13,14Whatever techniques are used,the reaction of the radars must be immediate and adaptive to prevent the ECM.
In this paper,we consider the problem of detecting the presence of deceptive jamming in the cell under test(CUT),and the aim of this paper is to approach the jamming detection problem as a signal processing-based ECCM technique.To achieve this aim,the behavior model of the deceptive jamming emitted by a DRFM jammer is introduced in Section 2,and the fingerprint feature of the spectra based on Volterra serial is also analyzed.In Section 3,we present a method of extracting this fingerprint feature.Besides,we build a detector exploiting the fractional Fourier transform(FrFT)to distinguish between echo and deceptive jamming.In Ref.15,the authors proposed a detector based on adaptive beamformer orthogonal rejection test(ABORT).The ABORT detector decides if the observed data contain a signal which belongs to one given subspace or a signal which belongs to an orthogonal subspace.The rejection of interfering signals was also considered.16–19In those papers,the authors solved the detection problem of extended targets embedded in homogeneous and partially extended interferences embedded homogeneous noise.These papers assume that targets and interferers are multidimensional and linearly independent signals.Unfortunately,for the real scenario,the echo and the deceptive jamming are generally not orthogonal,but their subspaces are different by an angle.20Thus,we modify the ABORT detector into our refined model to detect the presence of deceptive jamming only.Finally,we discuss a special case by extending our method to radar network.The numerical results are carried out by Monte Carlo simulation,which are described in Section 4,and we discuss the shortage and perspective of our method in Section 5.
2.Power amplifier distortion model
It is assumed that a phase array radar transmits a coherent linear frequency modulated(LFM)signal for target tracking.The basic structure of DRFM jammer is shown in Fig.1.Several procedures will introduce a nonlinear distortion.As is discussed in Ref.20,phase quantifier DRFM jammers will introduce a nonlinear distortion when quantization bits are low.Unfortunately,the advanced DRFM jammer is capable of quantifying intercepted signal in both amplitude and phase.Besides,the quantization bits are generally greater than 6-bits even when the sampling rate is greater than 2 GHz.Thus,it is not accurate for distortion analyses from the analog to digital converter(ADC)point of view.RF means radio frequency and DAC mean digital to analog in Fig.1.
As an essential part of the DRFM jammer,the power amplifier ensures that deceptive jamming remains a high power for combating against remote radars.Generally,the nonlinear behavior for the power amplifier can be analyzed in physical models using nonlinear coefficient model of the power amplifier.21,22For a simple case,we suppose that there is no time delay and false Doppler frequency modulated by the DRFM jammer.The additive noise is set to be zero.The input discrete pulse waveform can then be expressed as
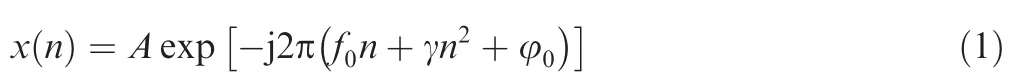
whereAis the amplitude,f0the video frequency of the DRFM output,γ the chirp rate,and φ0the initial phase.
As is discussed in Ref.22,considering the memory effect and polynomial structure,the distortion of power amplifier for a narrow band LFM input satisfies the Volterra series model.In order to meet the requirement of accurate modeling and low calculation burden,we consider a Volterra series model with memory depth of 5 and a Volterra order of 3,where the output power spectrum has a likelihood ratio greater than 95%compared to the ADS output through the simulations shown below.And there has little effect on likelihood ratio when a greater memory depth and Volterra order are chosen.The Volterra series model for the power amplifier output can then be interpreted as
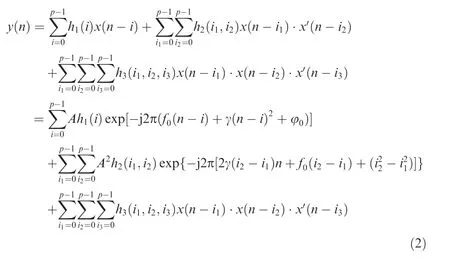
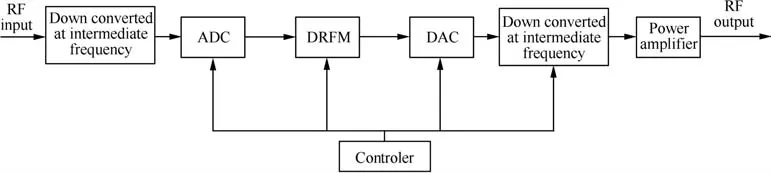
Fig.1 Basic structure of DRFM jammer.
wherepis the memory depth,h1(i),h2(i1,i2),h3(i1,i2,i3)are the Volterra kernels for different Volterra orders,and(·)'represents conjugation operator.
The first part in Eq.(2)can be expressed as
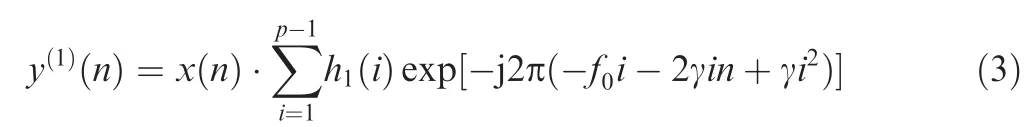
It can be regarded as an LFM signal with a compound sinusoid amplitude modulation.
The second part in Eq.(2)can be expressed as
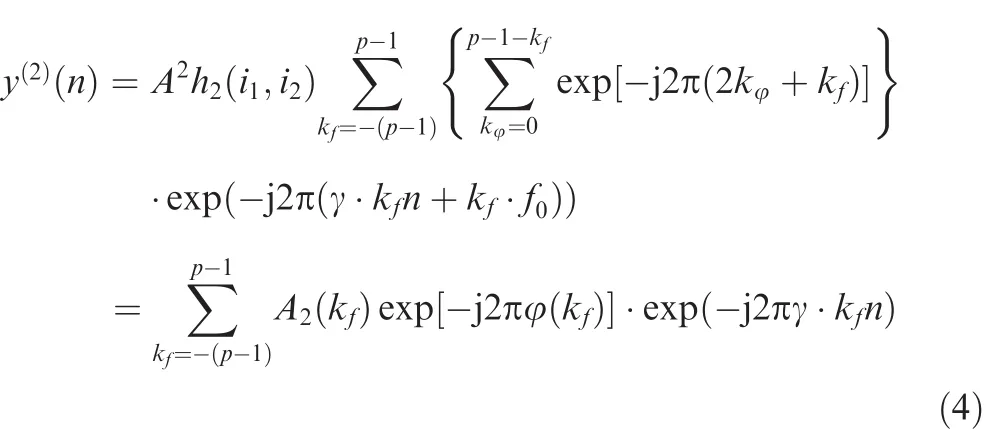
whereA2(kf)is the compound amplitude,φ(kf)the phase ofkfth component,andkfis the index gap between two components.For the case of conciseness,details on the derivation of Eq.(4)can be found in Appendix A.Eq.(4)indicates a group of spurious frequencies,and these spurious frequencies will lead to a nonlinear distortion.We note here that from experimental observation,these spurious frequencies mainly focus on high frequency range.
It is obvious that the third part in Eq.(2)has the same structure as Eq.(3).The components with higher Volterra order and greater memory depth have a limited power.22This means that the components can be ignored when their Volterra order and memory depth are high.Thus,analysis on the power amplifier distortion demonstrates that the output of power amplifier can be regarded as an LFM signal with a compounded sinusoid amplitude modulation in addition with a group of spurious frequencies.
3.Problem formulation
The echo and deceptive jamming are received by tracking radars.For the fundamental target detection scheme of radar system,the intercepted pulses are firstly down converted to intermediate frequency or video frequency and filtered with a low-pass filter with cutoff frequency ofFc,and then sample with a specific sampling frequency afterwards.We suppose here that the low-pass filter has a passband large enough to access the echo without distortion and some parts of the spurious frequencies are accessed in the passband.
3.1.Spurious frequencies component extraction
To quantify the distortion introduced by the power amplifier,we propose a method to detect the deceptive jamming(i.e.,detect the existence of the spurious frequencies).To serve this purpose,we assume that the discrete version of received echo and deceptive jamming without considering time delay and additive white Gaussian noise(AWGN)can be interpreted as

wherefI,fd,fjdenote the intermediate frequency,the Doppler frequency of the echo and the modulated false frequency,respectively.
We note here in Eq.(5)that the echo and jamming model is not accurate due to the amplitude modulation brought by target reflectivity.Fortunately,the amplitude modulation will not bring nonlinear distortion.The LFM component in Eq.(5)has the same behavior as a real target.More precisely,it lies in the same subspace or even in the same cone as is disscussed in Ref.20and may take the advantage of spurious frequencies.Thus,a pre-process to eliminate the primary component of the LFM is necessary.
The pre-process of the jamming detection can be conducted with following steps,and the spectrum is demonstrated in Fig.2 for easy understanding(The amplitude of spurious frequencies for field data is rather weak,and thus we amplified spurious frequencies in order to demonstrate the spectrum constitution.).The cutofffrequency of the low pass filter isFc=1.5×,whereBrepresents the bandwidth of the received signals.And the sampling frequency can be set to befs=3Bto avoid aliasing.The spectrum demonstration is shown in Fig.2(a).
Step 1.Dechirp with original transmitted LFM signal.
It is observed that the LFM component becomes a sinusoidal signal and spurious frequencies become a sequence of LFM structured signals.To simplify the analysis,we assume here that the cutoff frequencyFcis large enough.
The spectrum structure after dechirp is shown in Fig.2(b).
Step 2.Process a high-pass filtering to eliminate the baseband Dopller frequency/false Dopller frequency with a narrow stopband.Generally,which ensures that there exist at least two complete chirp components without aliasing after Step 2.
Step 3.Process FrFT on the received signal with rotate angle αr=arccot γ as Ref.23,and the output can then be interpreted as
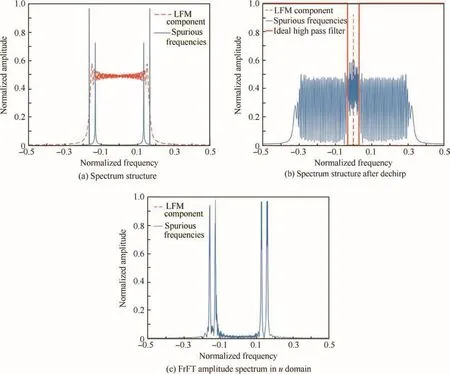
Fig.2 Spectra demonstration.
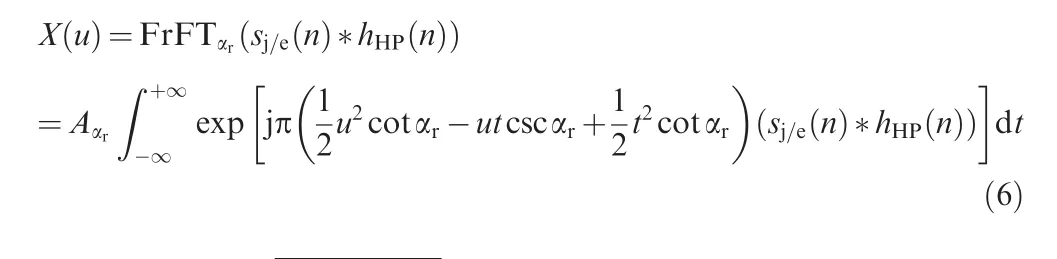
whereAαr=,hHP(n)denotes the ideal high-pass filter in Step 2,and*is the convolution operator.The amplitude spectrum inudomain is demonstrated in Fig.2(c).
From the spectrum demonstration,when there exist spurious frequencies,we can observe serval spikes in FrFT domain after pre-processing.On the other side,as assumption mentioned above,the amplitude modulation caused by target re flectivity will not introduce spurious frequencies.Thus,the amplitude spectrum in FrFT domain for the echo is approximately set to be zero after pre-processing.We design our detector regarding the spectrum structure after pre-processing.
3.2.Detection formulation
Similar to the ABORT test proposed in Ref.19,we assume that a phase array surveillance radar sensesKqrange bins containing target returns(including deceptive jamming or echo)andKsrange bins containing additive Gaussian noise only.The outputs of pre-process on each range bin are denoted by zk∈CN.TheseKqrange bins with returns constitute primary data andKsrange bins without returns constitute secondary data.We assume that each primary data is corrupted by an additive noise vector νk∈ CN,modeled as a complex normal vector with an unknown positive definite mean and a covariance matrix R ∈ CN×N.
Different from ABORT formulation,19it does not guarantee orthogonal property when spurious frequencies detection in FrFT domain is considered.Thus,we enhance target detection formulation in Ref.19by our jamming(i.e.,spurious frequencies)detection formulation.We make some adjustments to discriminateH1hypothesis that zkcontain spurious frequencies,and theH0hypothesis assumes that there is no nonlinear distortion.Therefore,we formulate our detection formulation as
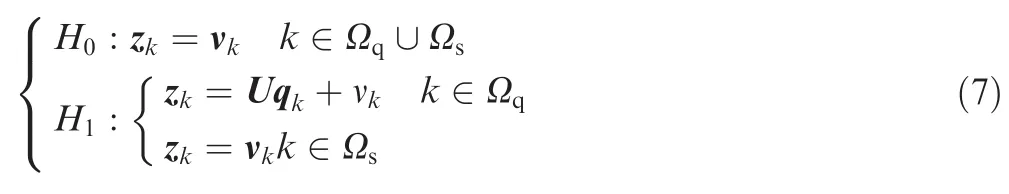
where Ωq={1,2,...,Kq} and Ωs={Kq+1,Kq+2,...,Kq+Ks}are index sets for primary data and secondary data.And we suppose thatKs≥Nto ensure that matrix S is invertible.Due to the random distribution of spurious frequencies,the subspace matrix U is unknown.We assume here U ∈ CN×Nwhereas rank(U)≤Nimplies the amount of independent spurious frequency components,and qkis a complex coefficient vector related to the amplitude and the phase of the spurious frequencies.
3.3.ABORT-like detector design
Based on the assumption above,we propose an enhanced ABORT detector in FrFT domain for jamming detection only.Actually,this section can be straightforwardly derived after some modification using results in Ref.15.
Z=[ZqZs]denotes the overall data matrix,where Zq=[z1,z2,...,zKq]∈ CN×Kqis the primary data matrix and Zs=[zKq+1,zKq+2···zKq+Ks]∈ CN×Ksisthesecondary data matrix.Moreover,letK=Kq+Ks,Q=[q1,q2,...,qKq]∈CN×Kqand S=be the covariance matrix based on the secondary data.(·)His the Hermit operator.
We now derive the two-step GLRT detector based upon primary and secondary data,which is tantamount to the following decision rule.19

wherefi(Z;·)is the probability density function(pdf)of Z under hypothesisHi,i=0,1.
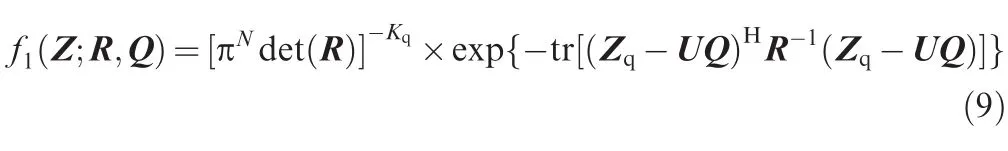
underH1hypothesis and
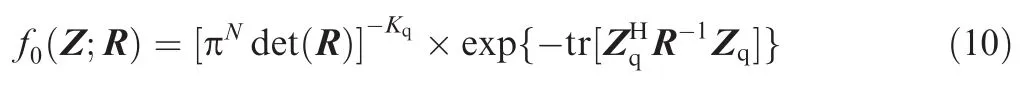
underH0hypothesis.
The maximum off1(Z;R,Q)with respect to Q can be calculated as
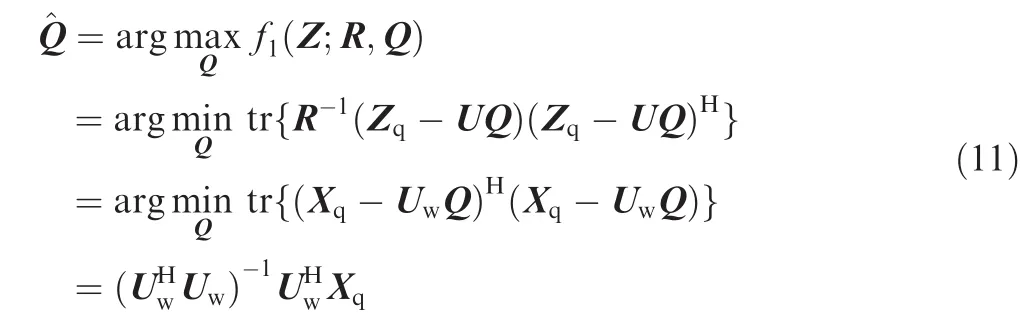
where Xq=R-1/2Zqand Uw=R-1/2U are primary data and spurious frequencies after whitening transform.Substitute Eq.(11)into Eq.(9)and we have a closed form of the pdf underH1hypothesis
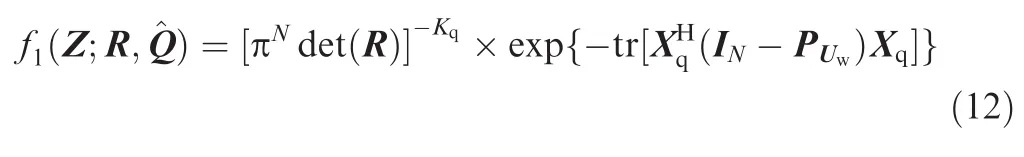
where PUw=is the whitening projection operator,and INis a unit matrix of sizeN.
Substituting Eqs.(10)and(12)into Eq.(8)and plugging S in place of R,16we have the compact expression
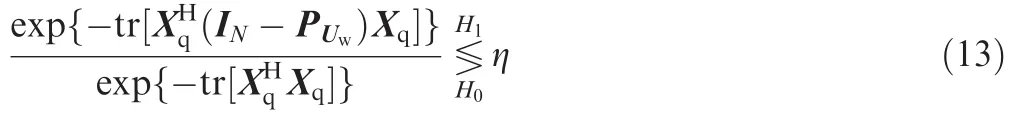
Take the natural logarithm and we obtain the adaptive ad hoc detector16based on primary data with subspace generalized adaptive matched filter(S-GAMF)structure,which can be interpreted as
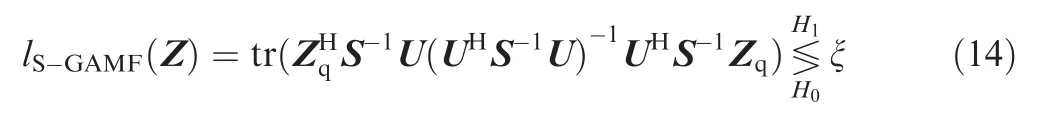
where ξ is a proper modification of the threshold.If the threshold is overwhelmed,a detection of jamming is declared.Herein,the detector does not guarantee CFAR properties in detecting targets as mentioned in Refs.15–19,but with the proper adjustment on the threshold according to different types of power amplifier,this detector will have a constant false detection probability on detecting jamming.
Herein,U remains an unknown subspace.Fortunately,it can be estimated according to the distribution of spurious frequencies after pre-processing in FrFT domain.Considering a sub-optimal case,since echo is approximately null after preprocessing,we assume that spurious frequencies lie in the subspace with full rank that U=INunder which circumstance the spurious frequencies spread randomly in FrFT domain.Thus,we have
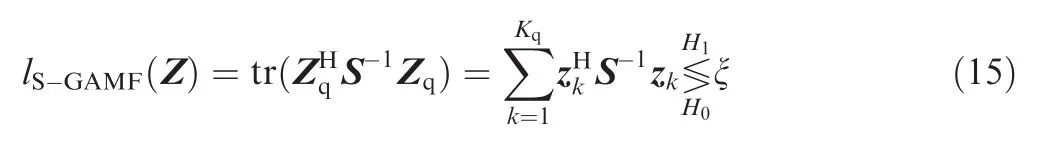
This detector has the same structure as ACE detector proposed in Ref.20whenKq=1.For ACE detector,the Maximum likelihood(ML)estimator of the spurious frequency vector is^s2ML=z(see Eq.(16)in Ref.20).Moreover,let^U=Zq,and the proposed detector has the same structure as Eq.(15).
In order to evaluate the jamming detection performance,we define here the false alarm probability to declare jamming existing under theH0hypothesis:
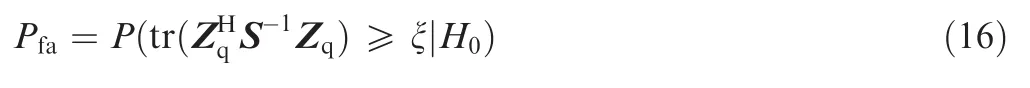
and the detection probability to declare jamming existing under theH1hypothesis:
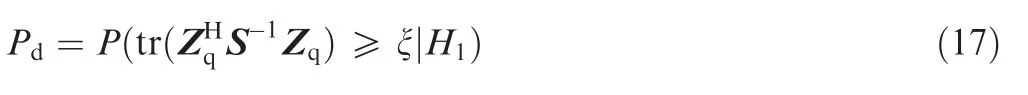
We note here that the false alarm probability and the detection probability are different from the false alarm rate and detection rate for traditional radar detections.
In summary,the jamming detection scheme is GRLT structured,and the likelihood ratio can be regarded as signal power in whitening space.Note that the detection probability and false alarm probability cannot be calculated in closed forms,so we resort to Monte Carlo simulations.
3.4.Expansion to radar network
Now we expand our result to radar network.In the specific surveillance area,all radars receive deceptive jamming.A team of DRFM carriers(jammers)modulates both time delay and frequency to generate false targets having the same motion behavior as real ones,which makes it difficult to distinguish false target from a real one through data processing.We use data processing in accordance with signal processing refereeing to reject false target through target tracking related methods.In Ref.16,the authors assume that a subset of the radar receives ECM signal,which sometimes cannot be satisfied under the circumstance of phantom track proposed in Refs.24,25.The demonstration of phantom track is shown in Fig.3.The circles named withRiindicate theith radar stations,the triangles named withEiindicate theith ECAVs and the points named withPiindicate the initial or the end of the phantom track.In our sketch,we show one phantom track namedP1.
To accomplish target identification,each radar station processes its inputs and transmits outputs to ‘fusion center”to obtain an over identification result.Generally,there are three levels for target identification of information fusion:
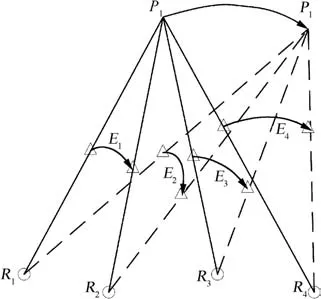
Fig.3 Demonstration of phantom track.
(1)Information fusion on raw data level.Namely,after some adjustment,all radars transmit their raw return to fusion center.
(2)Information fusion on feature level,where each radar station extracts a feature vector(e.g.,location of the targets)and transmits it to fusion center for information fusion.
(3)Information fusion on decision level,where each radar station processes target identification independently and makes an overall decision in the fusion center.
In this paper,we choose information fusion on decision level.Assume a radar network ofMradars,and each radar has a local decisiondi(i=1,2,...,M)where

The fusion center determines the overall decision for the system based on the individual decisions:

In Ref.26,an optimal detection system in radar network(or multiple sensors)is discussed.Since it is difficult to acquire the closed form of detection probability and false alarm probability,we choose three cases based on ‘k-out-of-N” decision fusion criterion as
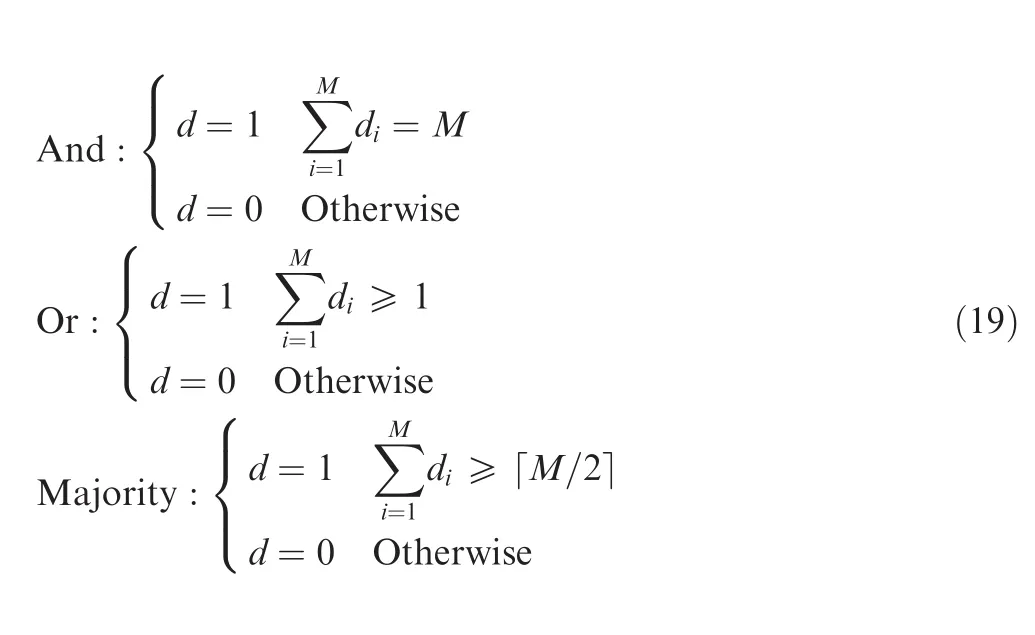
where ⌈·⌉is ceil operator.The result in Ref.26can be regarded as majority case.
4.Numerical results
In this section,we conduct some numerical simulations of our Monte Carlo performance analysis.
We first build a power amplifier model using ADS and the structure of power amplifier in ADS is shown in Fig.4.
In order to model power amplifier bahavior,we extract Volterra coffcients with respect to an ideal LFM input,considering a Volterra serial model with memory depth of 5 and a Volterra order of 3.Moreover,we set the input LFM signal to be produced with bandwidthB=3 MHz and pulse-width τp=64 μs,and the sampling frequency of the DRFM is set to befs=8 MHz.
To evaluate the error introduced by our proposed Volterra model,we show the power spectrum in Fig.5 with respect to the power amplifier modeled by Volterra series model,comparing output modulated by ADS with ideal LFM input.It is observed that our model has almost the same behavior as power amplifier output.
We define a likelihood ratio to quantify the error of the model as
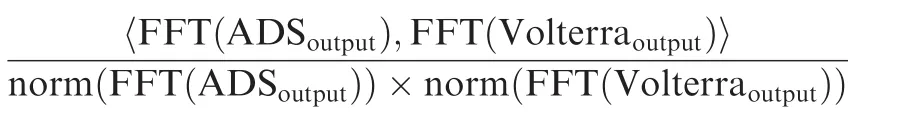
and the calculated spectrum likelihood ratio is 95.4%according to above equation when there is no AWGN.
To investigate the detection performance proposed in this paper for single radar,we consider a phase array radar tracking a moving target with an LFM signal as above.The radar is constituted of 8 antennas,has a coherent pulse interval(CPI),and includes 8 pulse repetitive intervals(PRI),PRI=1.6 ms.Thus,we haveKq=8×8 primary range bins andKs=8×8×(1600/64-1)secondary range bins.We apply the threshold guarantee cell averaging CFAR detection criterion as
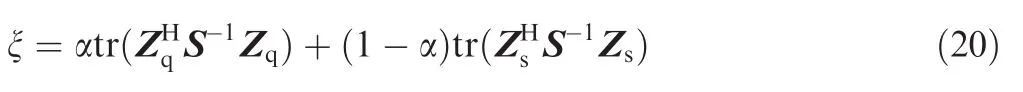
where α∈[0,1]is an adjustment factor which indicates different false alarm and detection performance.More precisely,detection performance is evaluated by resorting to 100 times of Monte Carlo counting techniques,versus signal to noise ratio(SNR)varying from 0 to 15 dB.
In Fig.6(a),we plot the curves of detection probabilityPdversus SNR of the proposed detector.As observed,the detection probability of jamming overwhelms 80%when SNR is greater than 5 dB.When SNR is higher,Pdis approximately 100%,whereas we note that the detection performance is poor when SNR is low.This is because when SNR is low,the colored noise takes the advantage of spurious frequencies.Especially,after dechirp is conducted in pre-processing,the noise is amplitude-modulated with a LFM signal,which will have a power gain in FrFT domain.This analysis is well proved in Fig.6(b)where we plot the curve of false alarm probabilityPfaversus SNR of detectors proposed.As observed,the false alarm probability is beneath 0.05 when SNR is greater than 5 dB,and approximately 0 afterwards,whereasPfaincreases rapidly when SNR is lower than 5 dB,with respect to our chosen threshold.This also indicates that the noise takes the advantage of spurious frequencies.
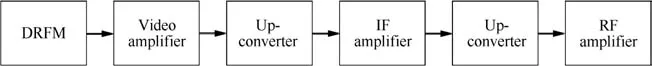
Fig.4 System diagram of power amplifier.
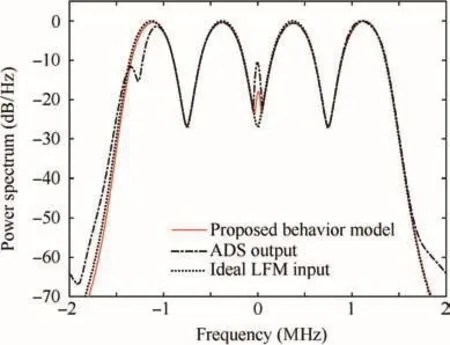
Fig.5 Power spectrum centered around 0 Hz.
In Fig.7,we present the effect on detection and false alarm performance with respect to the threshold.SNR varies from-5 dB to 15 dB and the adjust factor α varies from 0 to1.When α=1,the threshold is estimated from primary data only,and when α=0,the threshold is estimated from secondary data only.
When we set a definite adjustment factor α,it is observed that the detection probability will increase as SNR increases.Similarly,when we set a definite α,it is observed that the false alarm probability will decrease as SNR increases.The result is in accordance with the assumptions.Again,we note here that the detection probability denotes the probability to declare jamming existing under theH1hypothesis,and vice versa.It can be observed that the false alarm performance gets worse rapidly when α ≥ 0.9.Besides,when α ≤ 0.2,the detection performance gets worse rapidly.Meanwhile,the threshold has little effect on false alarm performance.Thus,it is reasonable to choose the adjustment factor from 0.4 to 0.6 to have a balance on detection performance and false alarm performance.
Now we expand our result to radar network as a special case.Since we conduct our detector on decision level,the topology has no effect on detection performance.We consider a scenario with 3 radars transmitting LFM signal with the same bandwidth and pulse width as above,but they have different carrier frequencies to avoid interference.The detection performance and false alarm performance with respect to different fusion criteria are shown in Fig.8.As observed,even though ‘Or” criterion has a rather low false alarm probability,the detection probability is still the lowest.For detection probability greater than 80%,the ‘Or” criterion loses about 2 dB compared to ‘Majority” criterion.This is in accordance with the result proposed in Ref.26.
In order to evaluate the performance with respect to different amount of radar stations,Fig.9 compare the cases when there are 3 radars in the radar network and 5 radars in the radar network through 100 times of Monte Carlo counting technique.As observed,with increasing amount of radar stations,the detection performance increases.This comparison indicates that the more radar stations are in the surveillance area,the better ECCM performance could be accessed.
As an illustration of effectiveness,we compare the proposed detector with ACE detector proposed in Ref.20(see Eq.(18)in Ref.20).The ACE detector has the formulation of
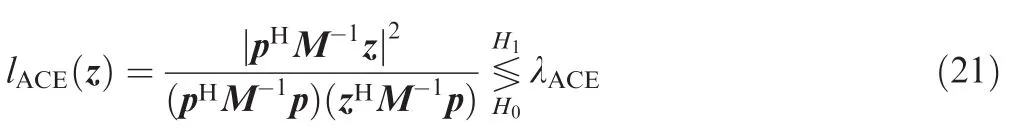
where p denotes real target’s steering vector which is assumed to be priori known,M is the estimation of correlation matrix,and λACEa CFAR threshold which can be found in lookup table.However,the Volterra serial model in simulations substitutes the phase quantization in Ref.20.We define here the probability of correct discrimination as
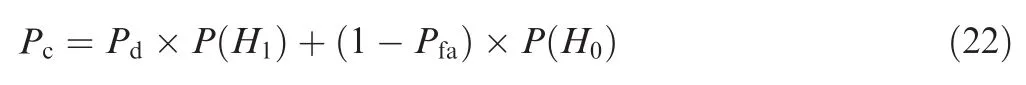
whereP(H0)=and false targets, respectively. In our simulations,and the other parameters are the same as the experiment in Fig.6.The comparison of the correct discrimination probability is shown in Fig.10.
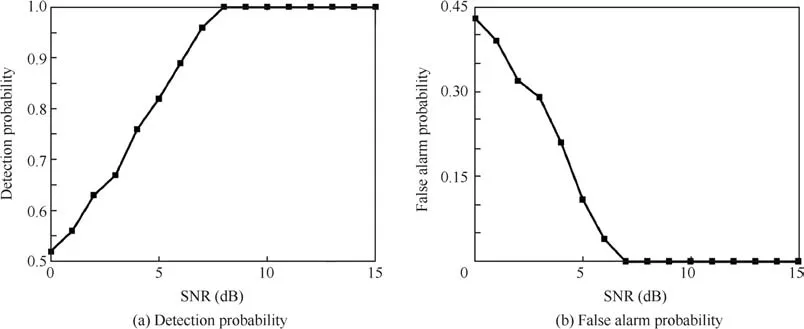
Fig.6 Detection performance of proposed detector.
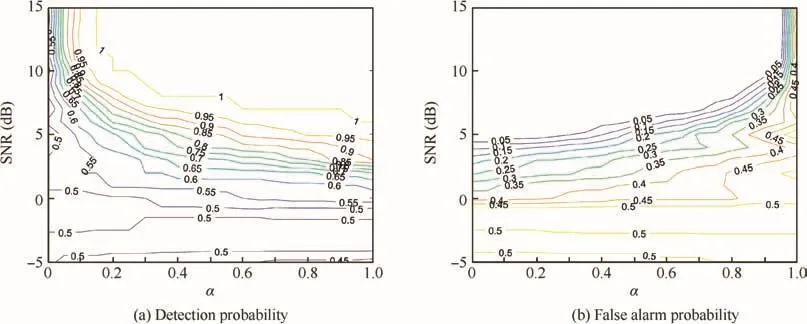
Fig.7 Contour of detection performance for proposed detector.
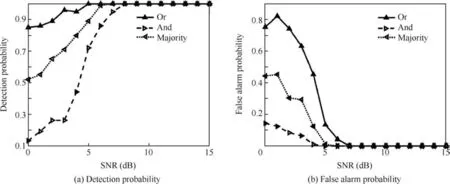
Fig.8 Detection performance of 3 radars.
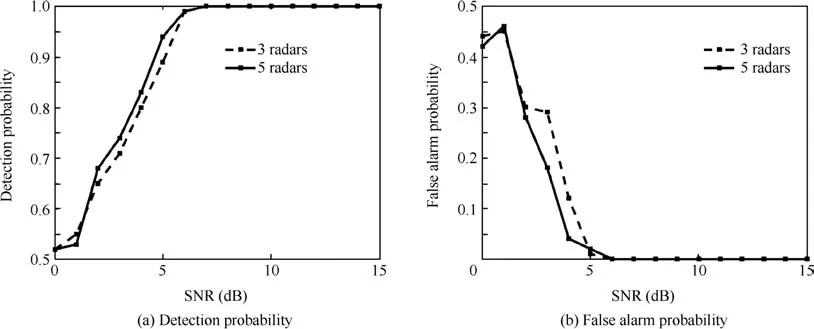
Fig.9 Detection performance comparison between 3 radars and 5 radars.
It is observed that the proposed detector overwhelms ACE detector by about 5 dB when the correct detection probability is greater than 80%.That is mainly because the ACE detector(as well as most detectors to discriminate deceptive jamming from echo)assumes that the phase quantization bits are rather low for radio frequency ADC.Therefore,the distortion is not obvious in time domain when SNR is low.However,the proposed detector detects the distortion in FrFT domain,which improves the performance in background noise.
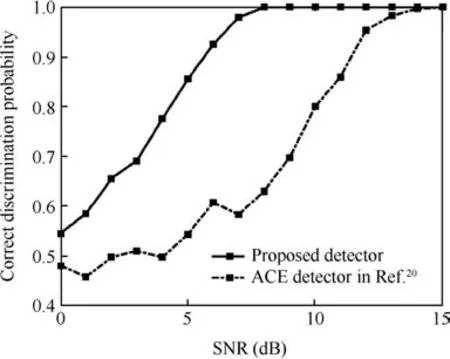
Fig.10 Probability of correct discrimination in ACE detector and proposed detector.
Based on these results,we conclude that the proposed signal processing based ECCM algorithm is capable of combating against deceptive jamming generated by the DRFM with distortion introduced by the power amplifier.In addition,this detection scheme can be extended to more complex radar signals(for instance,phase modulation)which satisfy the Volterra serial model.We note that the spurious frequencies may have different structures for different radar signals.Thus,it may require different pre-process procedures.However,the orthogonal property required in Refs.15–19may not be guaranteed.Furthermore,a similar idea of the proposed detector can also be extended to emitter recognition by exploiting the behavior of spurious frequencies.
However,there is a limitation that the spurious frequencies may not be obvious when SNR is rather low,and even though several papers studied the emitter recognition based on the Volterra serial model(which requires stricter accuracy on modelling),the identification results are still not robust enough.Besides,the detection is model-based and may not be applicable except for the power amplifiers of A-B type(which can be modeled as the Volterra serial model due to their memory effect and polynomial behavior).To solve this limitation and improve the robustness of adaptive detector,a more generalized model may be required.
5.Conclusions
(1)The problem of discriminating an echo versus a deceptive jamming is investigated in this paper.The structure of spurious frequencies introduced by power amplifier under Volterra model is also derived.
(2)By applying the GRLT detection criterion,an ABORT-like detector after dechirp pre-processing is proposed.The proposed ABORT-like detector devotes to the detection of spurious frequencies in FrFT domain.
(3)In the end,the performance of the proposed method in the presence of color correlated Gaussian noise is evaluated through numerical simulation.The computation results are in agreement with experimental data.The numerical results show that the detector is effective for detecting deceptive jamming.
Appendix A
Herein we derive the frequency structure for the second part of Eq.(2).
Letkf=i2-i1∈[-(p-1),p-1],and the actual time interval between two samples is Δts=1/fsj.Hereinfsjis the sampling rate of the DRFM.
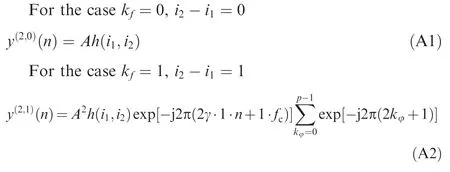
We obtain a sinusoidal signal with carrier frequency of γ/fjs.
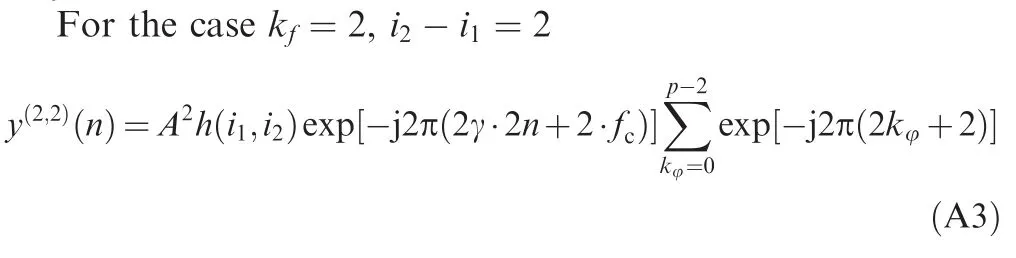
We obtain a sinusoidal signal with carrier frequency of 2 ·γ/fjs.Moreover,by mathematical induction,we can access the Eq.(4).
1.Neri F.Introduction to electronic defense systems.2nd ed.London:Artech House;1991.p.373–487.
2.Lu G,Tang B,Gui G.Deception ECM signals cancellation processor with joint time-frequency pulse diversity.IEICE Electron Expr2011;8(19):1608–13.
3.Lu G,Liao SN,Luo SC,Tang B.Cancellation of complicated DRFM range false targets via temporal pulse diversity.Prog Electromagn Res C2010;16(3):69–84.
4.Philip EP.Detecting and classifying low probability of intercept radar.2nd ed.London:Artech House;2009.p.110–3.
5.Xu J,Zhu S,Liao G.Space-time-range adaptive processing for airborne radar systems.IEEE Sens J2015;15(3):1602–10.
6.Luo SC,Tang B.An algorithm of radar deception jamming suppression based on the joint processing in spatial and polarization domains.Signal Process2012;28(3):443–8[Chinese].
7.Luo SC,Xiong Y,Cheng H,Tang B.An algorithm of radar deception jamming suppression based on blind signal separation.In:Hu B editor.Radar.ICCP 2001:Proceedings of the 2011 international conference on computational problem-solving;2001 Oct 21–23;Chengdu.Piscataway(NJ):IEEE Press;2001.p.167–70.
8.Gu HY,Xiong Y,Wang P,Luo SC,Li YP,Lu G,et al.Rangevelocity synchronous gate-pull radar jamming suppression with instantaneous cross-correlation.In:Zhou MQ editor.Radar.IEEE CIE 2011:Proceedings of the international conference on radar;2001 Oct 24–27;Chengdu.Piscataway(NJ):IEEE Press;2001.p.1839–42.
9.Behar VP,Kabakchiev CA,Doukovska LA.Adaptive CFAR PI processor for radar target detection in pulse jamming.J Signal Process Syst2000;26(3):383–96.
10.Slocumb BJ,West PD.ECM modeling for multitarget tracking and data association.In:Shalom YB,Blair WD,editors.Multitarget-multisensor tracking:applications and advances.Norwood(MA):Artech House;2000.p.395–458.
11.Blackman SS,Dempster RJ,Busch MT,Popoli RF.IMM/MHT solution to radar benchmark tracking problem.IEEE T Aero Elec Sys1999;35(2):730–8.
12.Li XR,Slocumb BJ,West PD.Tracking in the presence of range deception ECM and clutter by decomposition and fusion.Proceedings of SPIE-the international society for optical engineering;1999.p.198–210.
13.Zhao YL,Wang XS,Wang GY,Liu YH,Luo J.Tracking technique for radar network in the presence of multi-range-falsetarget deception jamming.Acta Electron Sin2007;35(3):454–8[Chinese].
14.Zhao S,Zhang L,Zhou Y,Liu N.Signal fusion-based algorithms to discriminate between radar targets and deception jamming in distributed multiple-radar architectures.IEEE Sens J2015;15(11):6697–706.
15.Pulsone NB,Rader CM.Adaptive beam former orthogonal rejection test.IEEE T Signal Proces2001;49(3):521–9.
16.Coluccia A,Ricci G.ABORT-like detection strategies to combat possible deceptive ECM signals in a network of radars.IEEE T Signal Proces2015;63(11):2904–14.
17.Coluccia A,Ricci G.A tunable W-ABORT-like detector with improved detection vs rejection capabilities trade-off.IEEE Signal Proc Lett2015;22(6):713–7.
18.Bandiera F,Besson O,Coluccia A,Ricci G.ABORT-like detectors:A Bayseian approach.IEEE T Signal Proces2015;63(19):5274–84.
19.Bandiera F,Besson O,Ricci G.An ABORT-like detector with improved mismatched signals rejection capabilities.IEEE T Signal Proces2008;56(1):14–25.
20.Greco M,Gini F,Farina A.Radar detection and classification of jamming signals belonging to a cone class.IEEE T Signal Proces2008;56(5):1984–93.
21.Pedro JC,Maas SA.A comparative overview of microwave and wireless power amplifier behavioral modeling approaches.IEEE T Microw Theory2005;53(4):1150–63.
22.Ding L.Digital pre-distortion of power amplifiers for wireless applications[dissertation].Atlanta(GA):Georgia Institute of Technology;2004.
23.Ozaktas HM,Kutay MA,Zalevsky Z.The fractional Fourier transform with applications in optics and signal processing.New Jersey:John Wileyamp;Sons;2001.
24.Xu Y,Basset G.Virtual motion camouflage based phantom track generation through cooperative electronic combat air vehicles.Automatica2010;46(9):1454–61.
25.Maithripala DHA,Jayasuriya S.Radar deception through phantom track generation.In:Tamer B editor.Radar.ACC 2005:Proceedings of the American control conference;2005 Jun 8–10;Maryland.Piscataway(NJ):IEEE Press;2005.p.4102–6.
26.He Y,Wang GH,Lu DJ,Peng YN.Multisensory information fusion with applications.2nd ed.Beijing:Publishing House of Electronics Industry;2007.p.61–87[Chinese].
15 June 2016;revised 10 September 2016;accepted 28 October 2016
Available online 7 June 2017
*Corresponding author.
E-mail address:zy_uestc@outlook.com(Y.ZHAO).
Peer review under responsibility of Editorial Committee of CJA.
Production and hosting by Elsevier
http://dx.doi.org/10.1016/j.cja.2017.04.014
1000-9361©2017 Chinese Society of Aeronautics and Astronautics.Production and hosting by Elsevier Ltd.
This is an open access article under the CC BY-NC-ND license(http://creativecommons.org/licenses/by-nc-nd/4.0/).
Adaptive signal detector;
ECCM capability;
Power amplifier;
Radar discrimination;
Signal processing
杂志排行
CHINESE JOURNAL OF AERONAUTICS的其它文章
- Wake structure and similar behavior of wake profiles downstream of a plunging airfoil
- Self-sustained oscillation for compressible cylindrical cavity flows
- Numerical studies of static aeroelastic effects on grid fin aerodynamic performances
- A new vortex sheet model for simulating aircraft wake vortex evolution
- Linear stability analysis of interactions between mixing layer and boundary layer flows
- Aerodynamic multi-objective integrated optimization based on principal component analysis
