Integrated Clustering and Routing Design and Triangle Path Optimization for UAV-Assisted Wireless Sensor Networks
2024-04-28ShaoLiweiQianLipingWuMengruWuYuan
Shao Liwei ,Qian Liping,* ,Wu Mengru ,Wu Yuan
1 College of Information Engineering,Zhejiang University of Technology,Hangzhou 310014,China
2 State Key Laboratory of Internet of Things for Smart City,University of Macau,Macau,China
3 Department of Computer and Information Science,University of Macau,Macau,China
Abstract: With the development of the Internet of Things (IoT),it requires better performance from wireless sensor networks(WSNs),such as larger coverage,longer lifetime,and lower latency.However,a large amount of data generated from monitoring and long-distance transmission places a heavy burden on sensor nodes with the limited battery power.For this,we investigate an unmanned aerial vehicles assisted mobile wireless sensor network(UAV-assisted WSN)to prolong the network lifetime in this paper.Specifically,we use UAVs to assist the WSN in collecting data.In the current UAV-assisted WSN,the clustering and routing schemes are determined sequentially.However,such a separate consideration might not maximize the lifetime of the whole WSN due to the mutual coupling of clustering and routing.To effciiently prolong the lifetime of the WSN,we propose an integrated clustering and routing scheme that jointly optimizes the clustering and routing together.In the whole network space,it is intractable to effciiently obtain the optimal integrated clustering and routing scheme.Therefore,we propose the Monte-Las search strategy based on Monte Carlo and Las Vegas ideas,which can generate the chain matrix to guide the algorithm to fnid the solution faster.Unnecessary point-to-point collection leads to long collection paths,so a triangle optimization strategy is then proposed that fnids a compromise path to shorten the collection path based on the geometric distribution and energy of sensor nodes.To avoid the coverage hole caused by the death of sensor nodes,the deployment of mobile sensor nodes and the preventive mechanism design are indispensable.An emergency data transmission mechanism is further proposed to reduce the latency of collecting the latency-sensitive data due to the absence of UAVs.Compared with the existing schemes,the proposed scheme can prolong the lifetime of the UAVassisted WSN at least by 360%,and shorten the collection path of UAVs by 56.24%.
Keywords: Monte-Las search strategy;triangle path optimization;unmanned aerial vehicles;wireless sensor networks
I.INTRODUCTION
In unmanned monitoring scenarios,WSNs play a critical role as sensing actors in IoT systems,to provide the information of interest to network users for the decision-making[1,2].Because sensor nodes are inexpensive,compact,environmentally tolerant,and adaptable,they can be easily deployed in a variety of environments(e.g.,the physical world,biological systems) for different applications (e.g.,agriculture,industry,smart cities,military,medical monitoring,environmental monitoring,etc.) [3-5].Big data applications have been widely deployed in various real-time data environments[6],and WSNs have become an important provider of big data[7].However,considering the inflexible energy replenishment and limited spectrum resources,it is challenging for WSNs to deal with the transmission of a massive amount of sensing data in an energy-effciient and low-latency way.
With the proposal and development of 6G networks,the Space-Air-Ground Integrated Network (SAGIN)has received much attention from researchers [8-11].As one of the key technologies of the emerging 6G networks,the SAGIN provides ubiquitous and seamless network connectivity and services by deploying communication platforms(e.g.,satellite networks,airborne networks,and terrestrial networks) at different altitudes [12,13].Driven by this,many researchers have proposed UAV-assisted WSNs for the collection of sensing data due to UAV’s beneftis of mobility,flexibility,and maneuverability [14].This type of data collection has the following advantages,and has also been proven to be an effective strategy [15]:1) Compared to traditional WSNs,UAVs can reduce the energy waste due to multi-hop communication,2)The distance over which sensor nodes transmit data is shortened,thus reducing the energy consumption of sensor nodes,and 3)UAVs can establish line-of-sight(LOS) links with sensor nodes with a high probability,thus having a better quality of the communication channel.
There have been previous protocols for wireless sensor networks [3,16-23],in which the network schemes can be broadly categorized into clustering schemes [17,24] and routing schemes [25,26].The introduction of UAVs has given the network more options for selecting cluster heads and transmitting data compared to traditional clustered networks.In the clustering phase of UAV-assisted WSNs,UAVs can assist the network in electing cluster heads.Compared to centralized cluster-based networks[24,27,28],UAVs can directly collect various data from sensor nodes about cluster head election,which greatly reduces the amount of data sent over the network and thus reduces the energy consumed by sensor nodes when rotating cluster heads.Work[29]proposed a data collection algorithm that leverages both the UAV and mobile agents to autonomously collect and process data when considering the density of network sensor nodes,the speed of UAVs,and data transmission conflicts.Nguyen et al.[30] derived a theoretical lower bound on the energy consumption of sensor nodes for transmitting data to the cluster head in uniform and normal deployments.Ebrahimi et al.[31]proposed the use of projection-based Compressive Data Gathering(CDG)in dense WSNs using UAVs as a new solution to reduce the energy consumption of the network.In addition,the UAV technology can improve the network deployment,e.g.,Pullwitt et al.[32]used UAVs to measure the coverage of wireless links and deploy WSNs accordingly.
In the current UAV-assisted WSNs,the clustering and routing schemes are determined sequentially.However,the two schemes are coupled,and the determination of one scheme would affect the setting of the other,so the sequential optimization scheme cannot fnid the optimal scheme of the lifetime as a whole.The lack of coverage due to the death of sensor nodes is instantaneous,but the recovery of mobile sensor nodes needs to take some time.Although its signifciance,the time difference between instantaneous death and delayed mobile recovery is rarely studied.In addition,some sensing data generated in the monitoring area is latency-sensitive,and thus its transmission would be delayed if waiting for the UAV to collect them.To avoid this issue,we need to design a mechanism for tight data transmission.In this paper,we aim to minimize the energy consumption of the network through shortening the path length of the UAV.The main contributions of this paper are as follows:
1.Considering the mutual coupling of clustering and routing,we design an integrated clustering and routing scheme.To reduce the computational complexity of integrated clustering and routing,we further propose the Monte-Las search strategy based on Monte Carlo and Las Vegas ideas.This proposed strategy can reduce the searching space of clustering and routing by generating the chain matrix to guide the algorithm to fnid the solution faster.
2.Unnecessary point-to-point collection leads to long collection paths,so a triangle optimization strategy is then proposed that fnids a compromise path to shorten the collection path based on the geometric distribution and energy of sensor nodes.To avoid the coverage hole caused by the death of sensor nodes,the deployment of mobile sensor nodes and the preventive mechanism design are indispensable.An emergency data transmission mechanism is further proposed to reduce the latency of collecting the latency-sensitive data due to the absence of UAVs.
3.For performance evaluation,we conduct a simulation experiment with a highly realistic environment using pipeline monitoring in a community in Shenzhen,China as an application scenario.We simulate the deployment of UAVs and sensor nodes to monitor the pipelines in the area and compare the results with traditional WSN and UAV-assisted WSNs.
The rest of the paper is organized as follows.Section II presents the system model and the problem description.Section III presents the algorithm for solving the optimization problem and describes the system implementation.The performance evaluation is presented in Section IV.Finally,the conclusions are given in Section V.
II.SYSTEM MODEL
2.1 Network Model
A wireless sensor network-based monitoring system can be roughly divided into two subsystems,the sensing system and the transmission system,where the sensing system is sensor nodes and the transmission system is the wireless sensor network composed of sensor nodes.To further improve the scalability and applicability of wireless sensor networks,this paper considers a UAV-assisted mobile WSN IoT framework,as shown in Figure 1.

Figure 1.The architecture of proposed UAV-assisted mobile WSN.
Taking the example of a sewage pipe monitoring system in a community in Shenzhen,China,the sensing system consists ofNmobile sensor nodes deployed in the community,which is to sense and collect information of interest to the users(such as the water level in the pipe,blockage,and pipe wall condition).The wireless sensor network composed of isomorphic sensor nodes is the transmission system,which is to process and transmit the collected data to the Internet access points(ISP,such as base stations and Sinks).In large-site application scenarios,relying solely on sensor nodes to transmit data can lead to rapid node energy consumption.To alleviate this situation,UAVs as part of the transmission system would assist the network in transmitting data.
As shown in Figure 1,we usesito denote theithsensor node with the 2D spatial coordinates being(xi,yi).The set of sensor nodes in the network is denoted as
The Euclidean distance between the sensor nodessiandsjcan be expressed as
In addition,the proposed UAV-assisted mobile WSN has the following properties:
• The sensor nodes in the network are divided into clusters.In each cluster,a sensor node is chosen as the cluster head to gather data from the other sensor nodes in the cluster and forward it to the ISP.Non-cluster-head nodes cannot communicate directly with the ISP and cluster heads of other clusters.Inter-cluster heads can use multihop communication to transmit data to the ISP.
• During each data collection cycle,the UAV gathers data from cluster heads along a pre-confgiured route.As this data collection is not real-time,the WSN can transmit data via communication between cluster heads when an emergency occurs.
• The clusters and cluster heads of are updated according to the status of sensor nodes in the network,and locations of sensor nodes can also be dynamically adjusted.
2.2 Energy Consumption Model
The energy consumption for sending and receiving data during wireless communication is considered.We adopt the radio energy dissipation model proposed in[18]to evaluate the energy consumption,as illustrated in Figure 2.Assuming transmittingl-bitdata,the energy consumption of the transmitter consists of the energy needed for encapsulating and transmittingl-bitdata,and the energy consumption of the receiver corresponds to the energy needed for de-encapsulatingl-bitdata.Letdenote the power consumption of processing 1-bitdata at the transmitter and receiver,respectively.Suppose that the distance between the transmitter and receiver isd.Therefore,the energy consumption at the transmitter can be expressed as
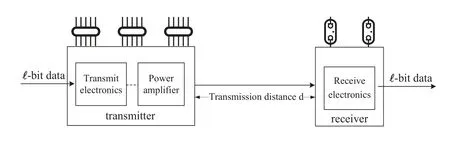
Figure 2.Radio energy dissipation model.
wherefmmeans the fading coeffciient.The energy consumption at the receiver can be expressed as
The energy consumption for aggregating eachl-bitdata,denoted byEDF,is expressed as
whereEDAmeans the power consumption of aggregating 1-bitdata.The main target of this paper is to minimize the network energy consumption,and meanwhile design a shortest data collection path for UAVs.Considering the mobile sensor nodes are deployed,we have to design the mobility scheme to avoid the coverage hole.Therefore,the Optimal Data Collection Path(ODCP) problem can be combined as Optimal Data Collection,Coverage,and Communication Problems(ODCCP).
III.PROPOSED PROTOCOL
In the proposed protocol,our objective is to determine an optimal network communication scheme among interconnected modules involving UAV paths,network coverage,movement distance of sensor nodes,clustering,and routing within the network.Specifcially,we propose a methodology named Integrated Solutions to jointly address these interdependent sub-problems.Meanwhile,we propose the Triangle Path Optimization strategy to reduce the length of UAV paths within the network.Additionally,we propose a novel strategy for generating chain matrices and for leveraging reinforcement learning (RL) to jointly accelerate metaalgorithms’search speed within the high-dimensional solution space.Furthermore,we design protective mechanisms for emergency transmissions and potential network coverage to ensure high-quality monitoring.
3.1 Protocol Model
As shown in Figure 3,the protocol model comprises several key components: solution design,Monte-Las Search Strategy,a Meta-heuristic algorithm based on RL,and protection mechanisms.Among these components,the solution design plays a pivotal role,delineating optimized collection paths for UAVs and communication schemes for WSNs.For the optimization of collection paths,we propose the Triangle Path Optimization strategy(TPO)as a secondary optimization to reduce redundant paths during pre-path planning.In the communication schemes of WSNs,the Integrated Solutions(IS)is proposed to jointly optimize coupling schemes.Subsequently,pending solutions are input into the encoding part and resolved by a Solver (a Meta-heuristic algorithm based on RL).Within the encoding part,we propose a Monte-Las search strategy(MLS)that amalgamates Monte Carlo(MC)with Las Vegas (LV) ideas to generate chain matrices.In the solver,we enhance the performance of meta-heuristic algorithms by utilizing RL to adjust fxied parameters within these algorithms.These two strategies can help algorithms quickly fnid a excellent communication scheme.Furthermore,we propose the emergency data transmission mechanism and preventive replenishment mechanism as protective measures to ensure high-quality monitoring and further refnie the communication scheme of the UAV-assisted mobile WSN.Finally,we analyze the convergence and computational complexity of the proposed strategies.
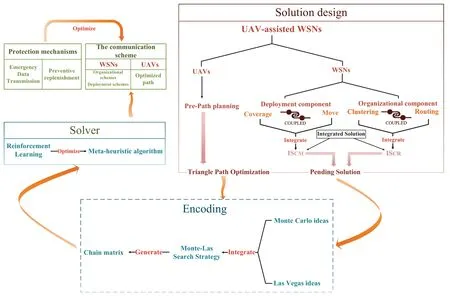
Figure 3.The relationship between different designs.
3.2 Solution Design
In this subsection,we introduce TPO and IS in detail.TPO aims to shorten the collection path of UAVs,while IS provides a methodology for solving coupled problems.
3.2.1 Triangle Path Optimization
In this subsection,we propose the triangle path optimization strategy to shorten UAV’s data collection path.As shown in Figure 4(a),assuming the existence of two cluster headsA,B,and a base station.The UAV departs from the base station,gathers data from sensor nodes,and returns to the base station.The conventional path is shown as the red line:UAV →A →B →BS.In practice,the UAV can communicate simply by stopping within the communication range of cluster heads,without the need for the UAV to be positioned above cluster heads to communicate.Therefore,it can fly to the midpointDof the line connecting two cluster heads to collect the data,with the path shown as the yellow line:UAV →D →BS.The path of the second is much shorter than the frist.Consider the case where there are three cluster heads,as shown in Figure 4(b).The red line still indicates the traditional path:UAV →A →B →C →BS.This path has the lowest energy consumption for cluster heads,but there is room for optimization for the path and the timeliness of the data.Instead of hovering above cluster heads to collect the data,the UAV can plan a shorter path,as shown by the yellow line:UAV →D →E →BS.
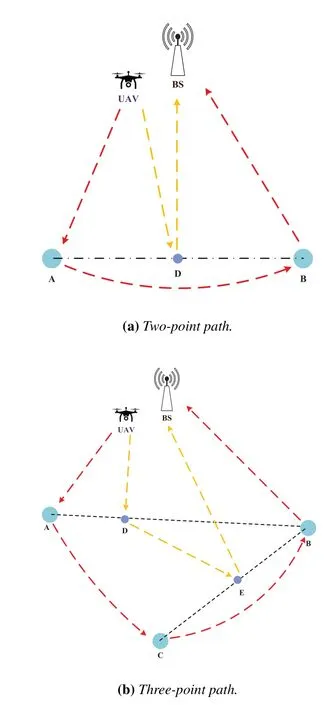
Figure 4.Path planning environment.
According to the preliminary path scheme,the TPO strategy is based on the idea of partitioning to fnid a straight line in the geometric distribution of each cluster head as a collection path to avoid unnecessary point-to-point collection.Considering UAVs alone,then the paths of UAVs can be reduced to very short ones as they do not need to fly for remote sensor nodes anymore.In practice,there are problems in the application.For example,simply reducing the flight path of the UAV may result in high transmission energy consumption for sensor nodes,which deviates from the original purpose of introducing the UAV to collect data.Therefore,TPO also needs to consider energy consumption of sensor nodes when optimizing the path.In summary,we can derive the triangle path optimization formula(TPOF):
whereηrepresents a TPO-optimized path planning scheme,andCHrepresents the set of cluster heads in the network.α,β,andδare the weighting factor,andEiis the residual energy of theithnode.ECiis the transmission energy consumption of theithnode.L(η) represents the flight length of the UAV inη.It is noteworthy that cluster heads may exhibit different energy behaviors for distinct path schemes.TPOF aims to fnid an optimization scheme that balances both the flight path and the energy consumption of sensor nodes,with the energy balance of sensor nodes being the key concern.TPO explicitly reduces the path,so it is crucial to ensure the energy consumption of sensor nodes as much as possible.Therefore,sensor nodes are considered in the second half of the TPOF and this is used to set the degree of inclination of the UAV’s flight path towards sensor nodes.For low-energy sensor nodes,the UAV also ensure point-to-point collection to save the energy of sensor nodes.
3.2.2 Integrated Solutions
The objective of IS is to adopt a parallel and unifeid solution when solving problems that are coupled or interconnected,thus avoiding sequential solving or fragmented optimization that can result in sub-optimal solutions.Figure 5 illustrates the difference between the two solutions.Taking ODCCP as an example in this work,when considering the deployment of sensor nodes,the stability of the network after the deployment is completed needs to be considered at the same time,and stability metrics include,but are not limited to,the network energy consumption and the size of coverage holes resulting from the death of sensor nodes.When considering the network communication scheme,clustering and routing in the protocol are considered as two aspects of a single problem at the same time.In this work,the coverage of sensor nodes and movement paths are integrated into an optimization schemeISCM,and clustering and routing of the network are integrated into the schemeISCR.

Figure 5.Difference between integrated and normal solutions.
3.3 Monte-Las Search Strategy
IS inevitably leads to a larger solution space,therefore we propose a Monte-Las search strategy that combines Monte Carlo ideas with Las Vegas ideas to accelerate meta-algorithms’ search speed within the highdimensional solution space.The search strategy has two phases.In the frist phase,a basic solution matrixMTotalis constructed according to LV.This process involves the meta-heuristic algorithm generating a solution matrixM1based on a requirementR1in Integrated Solutions.Subsequently,it generates a solution matrixM2requiringR2for each solution vectorinM1.If the solution matrix ofRiis not generated,a solution matrixMiis generated for each vectorinMi-1.After updating and evaluating matrixMTotal,the meta-heuristic algorithm obtains the synthetically optimal solution vectorvBest.In the second phase,following the MC,the meta-heuristic algorithm optimizes the solution vectorvBestand obtains the f-i nal solution vectorvFinal.The construction process of the chain matrix is illustrated in Figure 6.

Figure 6.Construction process of the chain matrix.
In the frist phase,LV ignores the fnial size of the solution matrix,but in reality,given the effciiency of the algorithm’s execution,the later the requirementRiis considered,the smaller the solution matrixMibecomes.
3.4 Parameters Selection Based on Reinforcement Learning
In the traditional genetic algorithm (GA),the crossover probabilitypcand the mutation probabilitypmare typically set as fxied values,which can compromise the effciiency of the algorithm.Therefore,in this paper,RL is applied to govern trends ofpcandpm.Each parameter has two trends,and their equations are expressed as follows:
In the above equations,αc,αm,βc,andβmare the fxied parameter affecting the basic step size of the change in the probability of both.itis the current number of iterations of the algorithm,andMax_Itis the maximum number of iterations.The above parameters together determine the change of thepcandpm.
Figure 7 illustrates the basic structure of RL.In this work,the Agent needs to fnid the most effective parameter update method to help the algorithm fnid the solution with a better ftiness value.The objective of maximizing the cumulative return of learning can be expressed as:
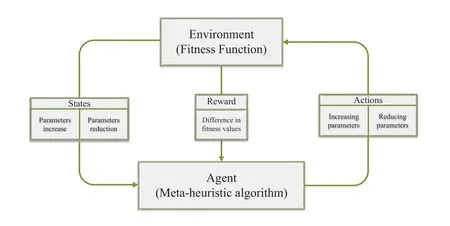
Figure 7.The basic structure of reinforcement learning.
whereγis denoted as the discount rate,andRt+kis the reward at timet+k.We can obtain the following updated formulation:
whereλis the learning rate,andγis the discount rate.st,st+1are the states at timet,t+1,respectively.atandat+1are the actions selected at the timet,t+1,respectively.R(st,at) is an immediate reward.Furthermore,the Agent’s strategy when taking action isε-greedy strategy.In this paper,the purpose of RL is to enable the algorithm to select parameters that are more benefciial for its population update,similar to a multi-armed slot machine in RL.Specifcially,the environment is the ftiness function,reward is the difference of the optimal ftiness value of the scheme before and after the update,and the actions are update equations chosen by the meta-heuristic algorithm for certain parameters (e.g.,(6) and (7)).The state are trends of parameters(e.g.,whetherpmandpcare increasing or decreasing).
In addition,parameters of RL change adaptively as the algorithm proceeds.Inε-greedy,the update formula ofεis
whereε0is the initial value,andεmaxis the maximum value.The update formula ofλis
whereλ0is the initial value,andλmaxis the maximum value.The update formula ofγis
whereγ0is the initial value,andγmaxis the maximum value.In the above three equations,theCε,Cλ,andCγare constant to control the learning time.The purpose of setting these parameters is to leave a stable time for the GA to fnid the best solution.countis the counter when reward is 0,which also controls the rate of change of the three parameters.Max_Itis the maximum number of iterations.
3.5 Protection Mechanisms
This subsection discusses protection mechanisms for WSNs to ensure high-quality monitoring.The main designs include the emergency data transmission mechanism and the preventive replenishment mechanism.
3.5.1 Emergency Data Transmission Mechanism
In UAV-assisted WSNs,it is diffciult for UAVs to collect data in real-time,which is unacceptable for some critical monitoring environments.Therefore,in this section,a transmission mechanism for emergency data is proposed.When an emergency occurs in the monitoring environment of a node,it can determine the message delivery method based on the status of the UAV.Figure 8 illustrates the transmission mechanism for three different states.

Figure 8.Emergency transmission mechanism.
In the UAV-assisted mobile WSN,it can be categorized into the following three states according to whether the UAV has completed data collection on sensor nodes or not: waiting,collecting,and completed.Nodes in different states have different transmission methods for emergency information:
•Waiting:When the nodesiwaiting for the UAV to collect data.sitransmits the data towards a relay node close to the base station.
•Collecting: When a nodesireceives an emergency message,it sends a request message to the UAV.At this point,after receiving the message,the UAV determines whether the nodesicontinues to transmit and its propagation route is reliable or not.If it is reliable,the nodesisend the message to its relay node.Otherwise,the UAV receives the emergency message and returns to the base station.
•Completed: When nodesireceives an emergency message,it sends it according to the relay node in the propagation direction that the UAV has set for it.
In this emergency transmission mechanism,the focus is on accuracy,real-time,and guaranteed arrival of messages.Therefore,when the UAV gather data,it sets a pre-arranged reliable propagation route for nodes.Given the limited storage capacity of sensor nodes,the UAV only determines relay nodes for sensor nodes.
3.5.2 Preventive Replenishment Mechanism
In the network,as surrounding sensor nodes dead,mobile sensor nodes in the network can redeploy sensor nodes to flil the coverage hole.There is a neglected time difference between death of sensor nodes,which creates an instantaneous coverage hole,and the redeployment of mobile sensor nodes,which takes a certain amount of time: the Time Difference between Instantaneous Death-Mobile Recovery(TDIM).
The preventive replenishment mechanism is shown in Figure 9.This work identifeis this problem and proposes a preventive replenishment mechanism.The preventive aspects of this mechanism are as follows:The base station periodically monitors the network.If the predicted future energy level of a sensor node falls below the warning energy thresholdEth,the base station will initiate measures to reduce the energy consumption of that sensor node.This is accomplished by relocating the node to an alternative location,preventing it from functioning as either a cluster head or a key routing location.In addition,before a node is about to run out of energy,the network redistributes the surrounding sensor nodes in advance to reduce the TDIM.For sensor nodes that are in critical positions of routing,sensor nodes with high energy levels are preferred to avoid network partitioning due to premature death.Preventive operations can signifciantly delay the death of sensor nodes,but scheduling sensor nodes to further postpone their demise becomes challenging when all the nodes in the network have low energy levels.
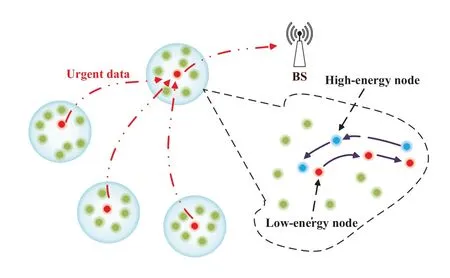
Figure 9.Preventive replenishment mechanism.
3.6 Performance Analysis of Strategies
This section analyzes the computational complexity and convergence performance of proposed strategies(MLS and TPO).AssumingYrequirements exist,theythrequirement generates a solution vector of sizePyusing MLS,resulti ng in the size of the chain matrix can be obtained asThe computational complexity of the GA isO(PgZ),wherePdenotes the population size,gdenotes the number of operations executed on the population in each evolution,andZdenotes the number of evolutions.Then the computational complexity of the GA with MLS can be calculated aswhereZ1andZ2denote the number of evolutions for the completion of the frist and second search phases,respectively.
The TPO proposed in this work is solved using GA.IfQclusters are divided into the network,the problem size becomesSubsequently,the computational complexity of resolving TPO with GA isis the population size generated based on the problem size.
The convergence performance of proposed strategies is depicted in Figure 10.ISCR,ISCM,andTPOare solved using GA.Typically,TPOconverges in 130 iterations,ISCRin 180 iterations,andISCMin 250 iterations.This demonstrates the excellent convergence performance of proposed strategies.

Figure 10.Convergence curve.
IV.PERFORMANCE EVALUATION
The application scenario of this experiment is pipeline monitoring within a community in Shenzhen,China,and the community is shown in Figure 11.The distribution of the pipeline is represented by two lines:green lines depict primary pipelines and orange lines represent sub-pipelines.The entire length of pipelines spans approximately 3418m.All the experiments are conducted in MATLAB 2021 environment.The base station is located at (450,450),which is shown as a blue dot in Figure 11.The 200 sensor nodes are distributed near the pipelines to monitor pipelines’ conditions.The initial battery energy of sensor nodes is 0.4J,the packet length is 4000 bits.The simulation parameters are shown in Table 1.

Table 1.Simulation parameter values.
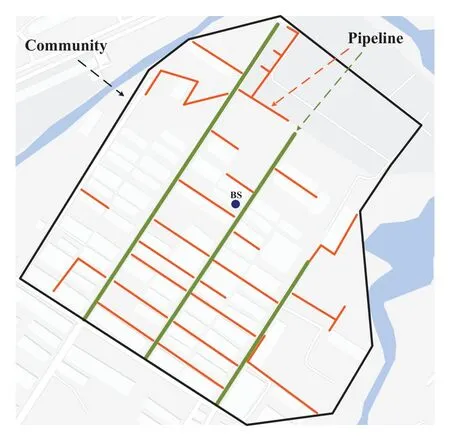
Figure 11.Experimental environment.
The main experimental evaluation indicators in this work include:
• Network lifetime: Network lifetime depends on the time to frist death of sensor nodes(FND),and FND is used as an important index of performance in this paper.
• UAV flight length: UAV flight length is defnied as the length that the UAV needs to fly to complete one round of data collection,which largely represents the information delay of UAV-assisted WSNs and the energy consumption of the UAV.
• Performance of TPO:Based on whether it is optimized by the TPO,it is defnied as the unoptimized flight length (UFL),the optimized flight length(OFL),the length difference value between them(DVBT),and the average optimization difference value(ADV),which represents whether the TPO is effective.The formula for calculating the average optimization difference value(ADV)is as follows:
whereOPcountis the number of optimizations,Distanceunis the flight distance before optimization,andDistanceopis the optimized flight distance.
To verify the effect of different parameters on TPO,we conduct experiments on different parameter combinations,and the specifci parameter combinations are shown in Table 2.αdenotes the degree to which the network prioritizes the shortest route.A lower value ofαindicates less emphasis on it.βrepresents the network’s energy strategy.A lower value ofβresults in a tendency for the network to employ a low-latency cycle for data collection,while a higher value ofβprioritizes protecting sensor nodes.
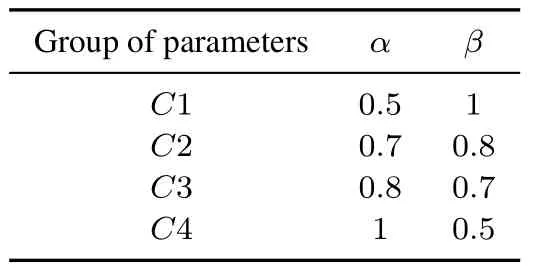
Table 2.Triangle optimization parameter combinations.
Figure 12 shows network lifetime of different combinations.It can be seen thatC2 has the best network lifetime,C4 has the worst network lifetime,andC1 andC3 are in the middle.The fnidings reveal an objective correlation betweenα,βand network lifetime.Increasingαand decreasingβgradually delays the time of FND.Whenβincreases from 0.5 to 0.7,the increase rate of FND is much faster than the increase from 0.7 to 1.This indicates that althoughβhas a guiding effect on the energy strategy of the network,the effect is weakened when the value of FND is high.The reason for this phenomenon may be that the order of magnitude difference between path length and energy is too large,and the trade-off parameter is not completely suitable for every parameter combination.On the other hand,as the ascent ofαincreases,the path taken by the UAV for collection is shorten gradually,resulting in a continued increase in the communication energy consumption of the node.This is comparable to the transfer of the UAV’s flight energy consumption to the node.C2has a slightly higherβthanC3,which makes the design of the network communication scheme slightly more focused on protecting the energy of sensor nodes,and therefore its FND is slightly better thanC3.

Figure 12.The number of alive sensor nodes per round.
Figure 13 compares flight paths under varying parameters.AsαinC4 is the largest,the TPO plans a shorter path for the UAV,resulting in the shortest flight path during its lifetime.C2 has a longer collection path due to its smallerα.The path length ofC3 is in the middle of the four combinations.In short,paths ofC2,C3,andC4 meet the original intention of settingαandβ.Due to the over-protection of node energy,C1 displays a highly unstable curve,resulting in the longest flight distance during the later stages.
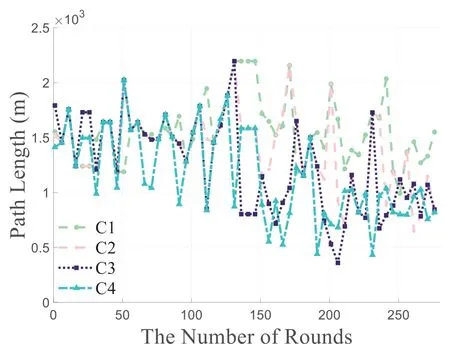
Figure 13.Comparison of flight path lengths.
Figure 14 illustrates influence of parameter values on TPO.The UFL ofC3 is long,which indicates that the death rate of network sensor nodes is slow and the UAV collects more rounds,which also indicates that this parameter combination is reasonable.Meanwhile,for the ADV indicator,C3 is optimal,which indicates that the algorithm is more sensitive to the search of the shortest path under this parameter combination.
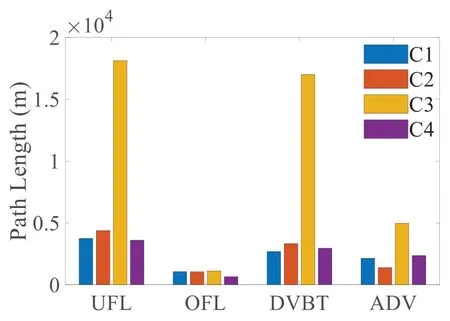
Figure 14.Comparison of triangle optimization parameter combinations.
Furthermore,the proposed scheme is compared with other schemes:
• GATERP(WSN)[22]: In this scheme,the WSN transmits data to the BS through sensor nodes.Furthermore,clustering and routing schemes are determined sequentially.
• UAV-assisted GATERP (UAV-WSN): In this scheme,a UAV can gather data from cluster heads in the WSN and transmit the data to the BS.Furthermore,clustering and routing schemes are determined sequentially.
• Proposed GATERP-based UAV-assisted mobile WSN (C1,C3,andC4): The scheme is derived by addressing ODCCP.
Figure 15 displays the fluctuations in the quantity of death of sensor nodes in each network architecture throughout the course of this situation.In large-scale environmental monitoring,traditional WSNs without UAV assistance show great limitations,as nodes die in the frist round.Furthermore,in comparison with a non-integrated solution for the UAV-assisted WSN,proposed solutions have the ability to fnid the most comprehensive network communication schemes.As a result,network stability periods forC1,C3,andC4 are more improved than that of other schemes.Additionally,the preventive replenishment mechanism can actively and dynamically adjust node positions,thereby prolonging network stability periods.

Figure 15.The number of alive sensor nodes per round.
Figure 16 shows path lengths of UAVs in different schemes.It is obvious that the path collection length without TPO is much higher than that of proposed network schemes,which indicates two points: 1) The data collection period in the network is longer and the effectiveness of the information is reduced.2)The energy consumption of the UAV is higher.

Figure 16.Comparison of flight path lengths.
V.CONCLUSION
In this paper,we propose the Integrate Solutions framework for the ODCCP and applied it to generate the network communication scheme.Considering the challenge of a larger solution space resulting from integration,we propose the MLS strategy and GA based on RL to expedite the search process.For TDIM,we propose a preventive replenishment mechanism to delay death of sensor nodes.For UAV’s collection paths,a triangle optimization strategy is proposed,which considers the geometric distribution of sensor nodes and residual energy to optimize the collection path.
In the future work,we will improve the negative effects of the TPO.Although it can signifciantly shorten the path length,there is a large uncertainty in the choice of parameters.We will optimize the heuristic formula of the strategy to reduce this uncertainty.In Integrated Solutions,although the chain matrix can reduce the search pressure,it still has great limitations for the Integrated Solution combining multiple problems,so it is necessary to explore more suitable and better search strategies.
ACKNOWLEDGEMENT
This work was supported in part by National Natural Science Foundation of China under Grants 62122069,62071431,62072490 and 62301490,in part by Science and Technology Development Fund of Macau SAR,China under Grant 0158/2022/A,in part by the Guangdong Basic and Applied Basic Research Foundation (2022A1515011287),in part by MYRG2020-00107-IOTSC,and in part by FDCT SKL-IOTSC(UM)-2021-2023.
杂志排行
China Communications的其它文章
- Distributed Application Addressing in 6G Network
- A Self-Attention Based Dynamic Resource Management for Satellite-Terrestrial Networks
- A Support Data-Based Core-Set Selection Method for Signal Recognition
- Actor-Critic-Based UAV-Assisted Data Collection in the Wireless Sensor Network
- Joint Task Allocation and Resource Optimization for Blockchain Enabled Collaborative Edge Computing
- Stochastic Gradient Compression for Federated Learning over Wireless Network
