混合攻击下时变信息物理系统的有限时域H∞控制
2020-04-11黎善斌胥布工
刘 珊,黎善斌,胥布工
(华南理工大学自动化科学与工程学院,广东广州 510640)
1 Introduction
In recent years,the rapid developments of calculation,control,communications and network technology,have expanded the way of the generic in interconnection between all things,greatly extended the information in time and space,and changed the organization evolutionary approach of physical systems,which have given birth to the cyber-physical system[1].Among many advantages and benefits that cyber-physical system(CPS)can provide,one of them is the integration of the physical system and cyber system which can create value,but at the same time,there are some related challenges and risks,one of which is security[2].
Security has always been an important consideration for CPS,which can be defined as the ability to ensure the communication between different components and prevent unauthorized server access[3].In a CPS,the protection of data and communication is difficult,so security is a complex and challenging task,this is because of the combined architecture of data,communications,process,and communication channel.The security problems of CPS in power grid systems,smart transportation systems,medical systems,water treatment system and other areas have received considerable attention in some literatures,and the security analysis and research of CPS under adversarial attacks has become a hot topic[4–6].
Among various target objects which adversary could attack,the communication channel is the most common object.This is because the communication channel which transmits measurement or control data is usually connected via hard-wired or wireless networks,and the attacker can conduct DoS attacks through the networks to make the data packet dropouts[7–8].A lot of recent researches have focused on the DoS attacks[9–12].With the energy constraint of the jammer and the existence of attack detection device,the jammer can not always successfully cause the packet dropouts of the communication channels[13–14].Thus some researches have presented that the sensor data packet will be dropped randomly during the DoS attack period with a certain probability,and can be modeled by independent and identically distributed(i.i.d.)Bernoulli variables[15–18].The research in[16]considers the optimal control feedback controller that minimizes a given objective function subject to safety and power constraints for a class of denial-of-service(DoS)attack models.In[17],the authors focus on the optimal control and scheduling problem for linear networked control systems under DoS attacks,which can jam the communication channel between the remote sensors and the controller.To solve the problem,a zero-sum static game of complete information is first utilised to investigate the optimal strategies for both the trigger and the attacker.Besides the communication channel,the sensor and actuator are also the common objects which adversary could attack.For example,false data injection(FDI)attacks can inject false information into sensors or actuators,and cause the measurement or control data destroyed[19–23].Mo et al.consider the case that the attacker can design his actions to inject error information into the sensor without being detected,and study the effect of false data injection attacks on state estimation[19].The authors in[23]consider the scenario that a continuous-time,linear time-invariant(LTI)system withMinputs andPoutputs are controlled and measured by vulnerable actuators and sensors,respectively.A new notion of controllability and observability for CPSs under actuator attacks and sensor attacks has been introduced to analyse safety performance.Since many commercial devices are readily available for adversary to conduct these attacks,similarly,many attack strategies have been mentioned in some papers,we can know these attacks are already serious threats for the CPS[24–25].
In practical engineering applications,for example,complex system process,intelligent robot control and the aerospace industry,the time-varying phenomenon of controlled system is common,whether the parameter of the system is time-varying or the structure is timevarying.Thus,more and more attention has been paid to it by researchers from different perspectives.Some of the previous researches have focused on the H∞control/filtering problem for time-varying system[26–27],and several kinds of approaches have been used for solving this problem,including the game theoretical approach[27–28],the differential/difference linear matrix inequality(DLMI)and recursive linear matrix inequality(RLMI)approach[29–32],and the backward recursive Riccati difference equation approach[26,33–34].On the other hand,the control objects sometimes are required to be completed in a limited time,such as missile interception,satellite orbit,etc..In addition,if the system is under attacks,the adversary can’t always successfully launch attacks with the same attack strategy due to the energy constraint of attacker or the existence of defense strategy.Therefore,considering these actual cases,the secure control problem for the time-varying system under attacks in a given finite-horizon has practical research significance,and to our best knowledge,it has not been properly researched so far,then to shorten this gap,this problem will be researched in this paper.
Based on the above discussion,we focus on the security problem of CPS under hybrid attacks,including DoS attacks on the sensor communication channel,and FDI attacks on the sensors and actuators.Assuming that the attacks period is given,the DoS attacks can be described by the Bernoulli distributed white sequences with known probability as the previous researches[15,17],and the FDI attacks signals injected in the sensors and actuators are unknown but norm bounded[35–36].It has the theoretical and actual meaning to research the impact from these attacks on the performance of timevarying system in a finite horizon.Therefore,we target at designing a output feedback controller by using the stochastic analysis techniques,some sufficient conditions are established to guarantee the H∞performance in a finite-horizon for the addressed system by using backward recursive Riccati difference equation approach.The main contribution of this paper is mainly as following three points:i)both the DoS attacks and FDI attacks are considered in the output feedback controller design for the time-varying system which has multiple sensors and multiple actuators;ii)a sufficient condition is given for the controller design which makes H∞performance from the attacks signals to controlled output satisfied;iii)a suboptimal controller design algorithm is proposed by solving double backward recursive RDEs.
The contents of the paper are as follows.In Section 2,the mathematical models of the CPS under hybrid attacks are described,and main control objective is presented.Then the main results are given in Section 3.At last,numerical simulation and conclusion are given to demonstrate the validity and applicability of the proposed approach in Section 4 and Section 5,respectively.
Notations:We use a fairly standard notation in this paper.denote,respectively,thendimensional Euclidean space and set of alln×mreal matrices.denotes the set of integers(positive integers,negative integers).The notationXY(X >Y),whereXandYare real symmetric matrices,means thatX −Yis positive semi-definite(positive definite).E{x}and E{x|y}will,respectively,denote the expectation of the stochastic variablexand expectation ofxconditional ony.0 represents the zero matrix of compatible dimensions.Then-dimensional identity matrix is denoted asInor simplyI,if no confusion is caused.The shorthand diag{·}stands for a block-diagonal matrix.∥A∥refers to the norm of a matrixAdefined byMTrepresents the transpose ofM.
2 Problem formulation
Consider a discrete time-varying linear CPS model with multiple sensors and multiple actuators shown in Fig.1.The output signal transmission is implemented between the sensors and remote controllers via network channels,which can be jammed by the DoS attacks;meanwhile,there arenysensors andnuactuators which can be injected in unknown random attack signals by the FDI attacker.

Fig.1 The structure of CPS with hybrid attacks
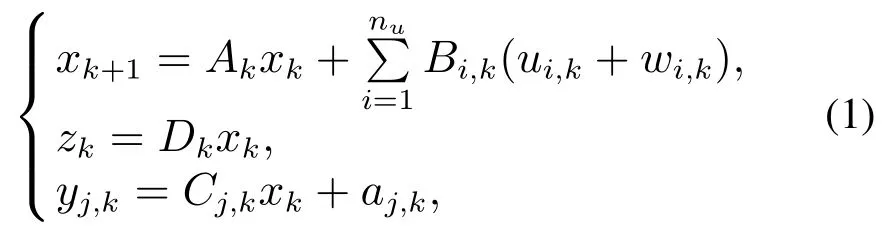
The plant is a discrete time-varying system defined in the finite horizonk ∈[0,N]of the form wherei ∈{1,2,···,nu}represents theith actuator,j ∈{1,2,···,ny}represents thejth sensor,is the state vector,is the control signal input to theith actuator,is the attack signal injected into theith actuator which belonging tol2[0,N],is the controlled output,yj,k ∈is the output of thejth sensor,is the attack signal injected into thejth sensor which belonging tol2[0,N]andandCj,k ∈are known real-valued time-varying matrices.
Remark 1Some previous researches have presented the model of sensor attacks and actuator attacks for linear time-invariant system,and assumed that the attack signals have bounded energy in a finite-horizon[23,35].Inspired by these works,the time-varying CPS model subject to FDI attacks in sensors and actuators is given in(1),and the attack signalswi,kandaj,kare priori-unknown and energy bounded.If the attack signalwi,k=0,it means that theith actuator is not attacked;otherwise,theith actuator is successfully attacked by adversary,the output of theith actuator is false.Similarly,the attack on the sensor can affect the accuracy of the measured output data[37].The FDI attacks are unpredictable,and the attack signals can destroy the performance of the system,so that the influence of attack signals on the controlled output is worth studying.
Considering there are random DoS attacks occurring between the sensors and controllers on the S–C network channels,then the measured output model with S–C packet dropout can be expressed as

Remark 2Similar to the setup in some previous research[16,18,38],the occurrence of packet dropouts caused by the DoS attacks is stochastic and its probability is known.Then the stochastic variableαkis Bernoulli distributed with white sequence taking the values of 0 and 1,whose expected valueis known constant which means that each packet exchange attempt faces an attack with a fixed probability.If the communication channel between thejth sensor to controller is jammed by the DoS attack,then the output data packet will be dropped.
The controller can be expressed as

Then the closed-loop system by substituting(2)and(3)into(1)as follows:

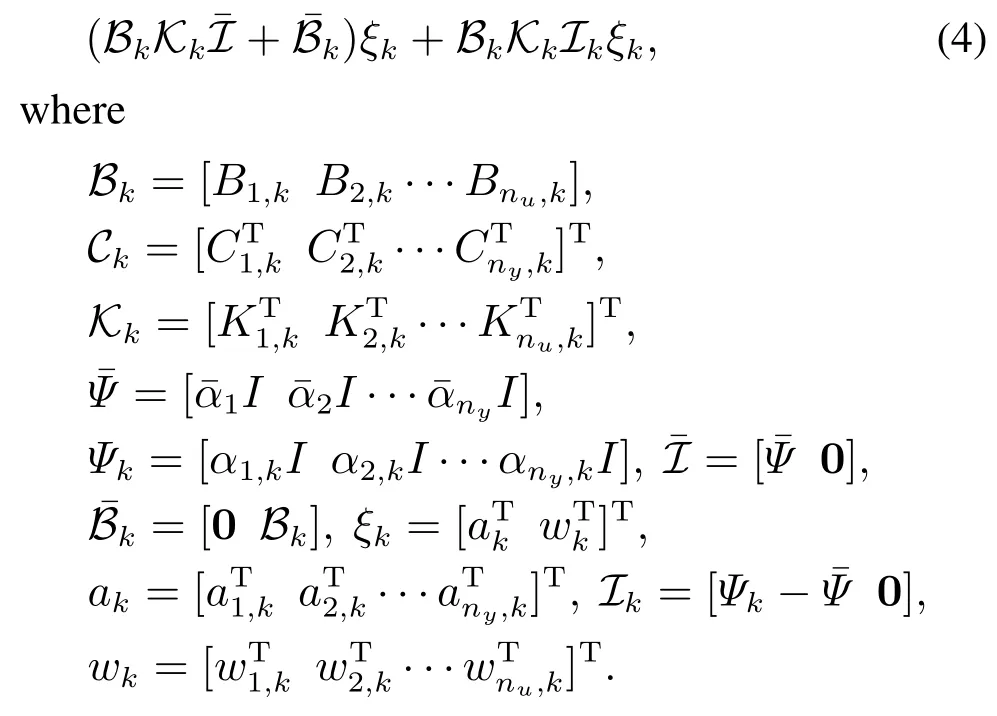
The main problem addressed in this paper is described as follows.
Problem 1For the given finite time horizon[0,N],positive scalarγ,positive definite matrixWand initial statex0,we aim to design appropriate controller parametersKi,k(i ∈{1,2,···,nu})such that,the closed-loop system(4)satisfies the following H∞performance requirement:

Remark 3The problem which requires H∞performance gain from disturbance signal to controlled output less than a given constant has been researched in previous works[16,18,39].Based on these works,if the injected signalswandaare disturbance signals,the H∞performance requirement(5)can also be regard as that from disturbance signal to controlled output in a finite horizon.
3 Main results
Lemma 1LetU,VandWbe known nonzero matrices with appropriate dimensions.The solutionXto
Lemma 2Given the attack attenuation levelγ >0 and the positive matrixW.For any nonzeroξk,the closed-loop system(4)satisfies the H∞performance requirement(5)for any nonzero attack signalξk,if there exists a family of non-negative definite matricesPk(0kN,with the final conditionPN+1=0)and a set of real-valued matricesKksatisfying the following backward recursive RDE:
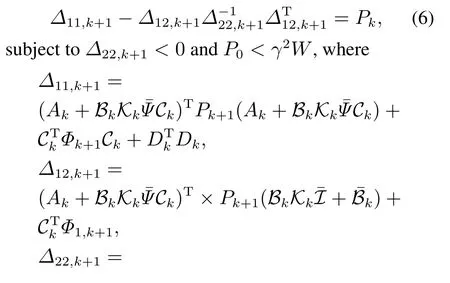
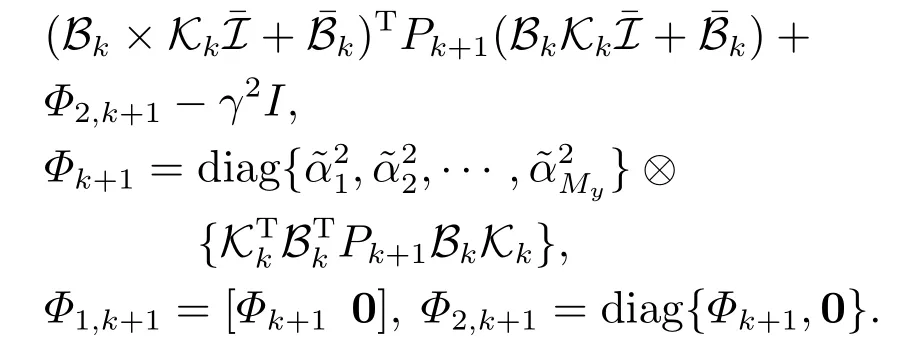
So far,we have conducted the H∞performance analysis in terms of the solvability of a backward Riccati equation in Lemma 2.In the next stage,let us propose an approach for computing the suboptimal controller parametersKi,k(i ∈{1,2,···,nu})in each step under the worst situation,i.e.On this condition,we rewrite the closed-loop system(4)as follows:
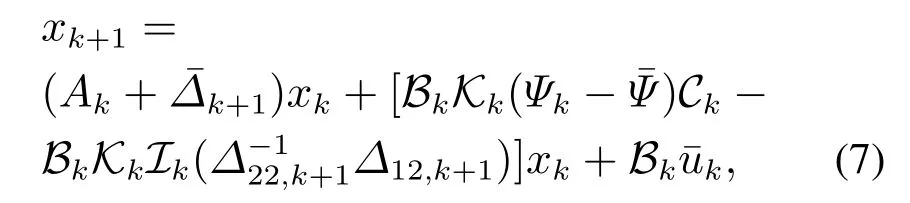
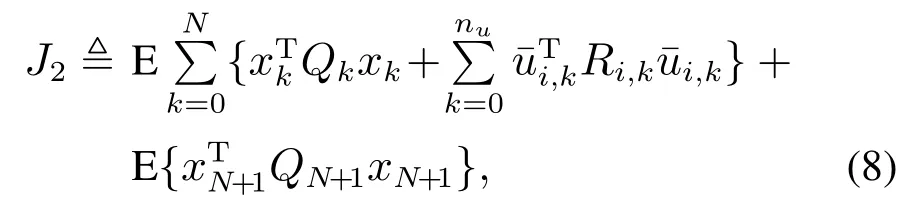
whereQk0 andRi,k >0(i ∈{1,2,···,nu})are the known weighting matrices.
Problem 2By employing the worst-case FDI attack,we aim to provide a design scheme of the controller parametersKkto minimize the linear quadratic performance functionJ2as described below:

subject to Problem 1 and system dynamics(7).
Then we will solve the Problem 2 by giving the following theorem.
Theorem 1Given the attack attenuation levelγ >0 and the positive matrixW.For any nonzeroξk,the closed-loop system(4)satisfies the H∞performance requirement(5)for any nonzero attack signalξk,if there exist two families of non-negative definite matricesPk,Sk(0kN)and a set of real-valued matricesKksatisfying(6)and the following backward recursive RDE:
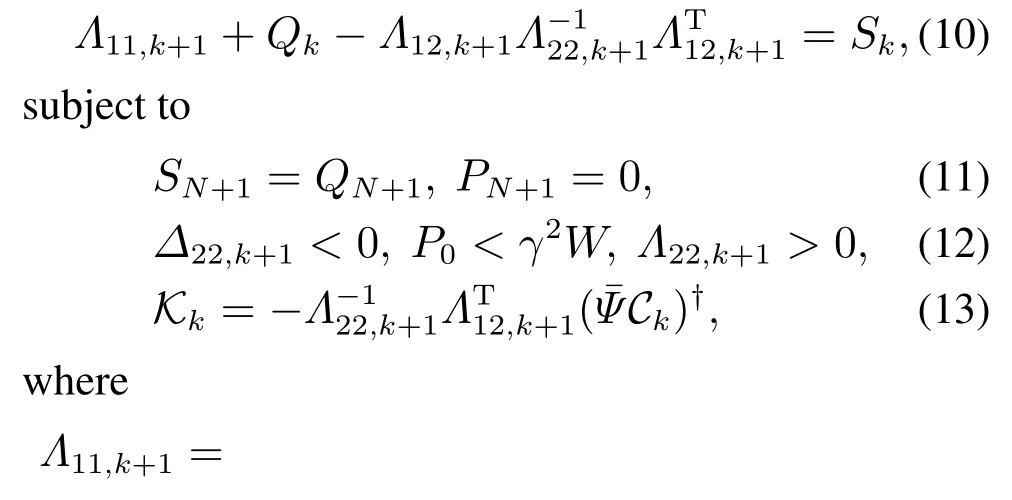

ProofFirstly,it follows from Lemma 2 that,if there exist solutionsPkandKkto(6),(11)and(12)so that the system(4)achieves the pre-specified H∞performance(5).On this condition,the worstcase attack signal can be expressed asξk==By employing the worst-case attack,the closed-loop system(4)can be written as(7),then the cost functionJ2can be described by completing the square with respect to

For the purpose of minimizing the cost function(8),the controller parametersKkcan be selected in each iteration backward as follows:

It follows from Lemma 1 that(13)is the solution of the optimization problem(15).The proof is complete.
QED.
However,we can see from the above theorem that it is difficult to get theKkfrom(13).Then in order to obtain the controller parametersKkdirectly and simplify the calculation process,the following theorem is given.
Theorem 2Given the attack attenuation levelγ >0 and the positive matrixW.For any nonzeroξk,the closed-loop system(4)satisfies the H∞performance requirement(5)for any nonzero attack signalξk,if there exist the positive scalarhk,two families of nonnegative definite matricesPk,Sk(0kN)and a set of real-valued matricesKksatisfying the following two backward recursive RDEs:

ProofDefinewherehk >0 is introduced to provide more flexibility in the controller design.Then denotethe closed-loop system can be described as

It follows from Theorem 1 that if there exist solutions{(hk,Pk,Qk,Kk)}0≼k≼Nsatisfying the backward recursive RDEs(16)with(17)–(18),then the system satisfies
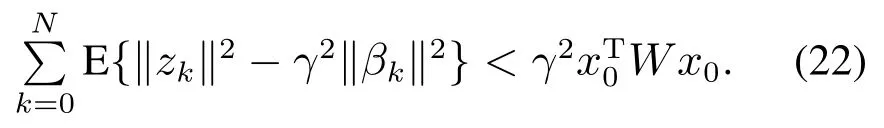
If the condition(20)is satisfied,we can get

which implies that the H∞performance constraint(5)is satisfied.Then for the purpose of minimizing the cost function(9),the suboptimal controller parametersKkcan be selected in each iteration backward as follows:
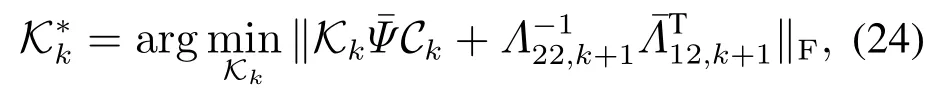
which equal to calculate

It follows from Lemma 1 that(19)is the solution of the optimization problem(25).The proof is complete.
QED.
Noticing that the controller parametersKkare involved in the proposed double RDEs,by means of Theorem 2,the finite-horizon H∞controller design algorithm is proposed as follows.
Algorithm 1finite-horizon H∞controller design:
Given:N,QN+1,γ,W,Qk,Rk;
Output:Kk,Pk,Sk,
wherej ∈{1,2,···,ny},k ∈{0,1,···,N}.
Steps of algorithm:
1)Initializek=N,SN+1=QN+1,PN+1=0;
2)Select the appropriate valuehk,computeandΛ22,k+1>0,then the controller parametersKkcan be solved by(19),and go to the next step,else jump to Step 7);
3)If the condition(20)is satisfied,go to the next step,else return to Step 2);
4)Solve the backward RDEs(16)to getPkandSk;
5)Ifk0,setk=k−1,and go back to Step 2),else turn to the next step;
6)If the conditionP0<γ2Wis satisfied,this algorithm is feasible,and output the results,else go to Step 7);
7)This algorithm is infeasible.
Remark 4In this paper,the finite-horizon H∞controller is designed for a time-varying system with multiple actuators and multiple sensors under FDI attacks and DoS attacks by solving double backward recursive RDEs.Note that Lemma 2 and Theorem 1 are proved mainly by the completing the square method which leads to very little conservatism,and Theorem 2 is given to obtain the controller parametersKkdirectly and simplify the calculation process,which also provides more flexibility in the controller design.We can see from Algorithm 1 that,there are several factors that can increase the complexity of controller design,including the time-varying system parameters,the prescribed attack attenuation levelγ,the selected scalarhk,and the probabilities of packet dropouts from sensors to controllers caused by DoS attacks.Therefore,the comprehensive influence of these factors will determine the control effect,and in actual implementation of the Algorithm 1,in order to obtain the better control effect,in the case that the system parameters and the probabilities of packet dropouts are known,we will adjust the scalarhkappropriately to get a smaller prescribed attack attenuation levelγ.
4 Numerical simulation
In this section,we aim to demonstrate the effectiveness of the proposed problem and algorithm.
Consider a discrete-time time-varying system with the following system parameters:
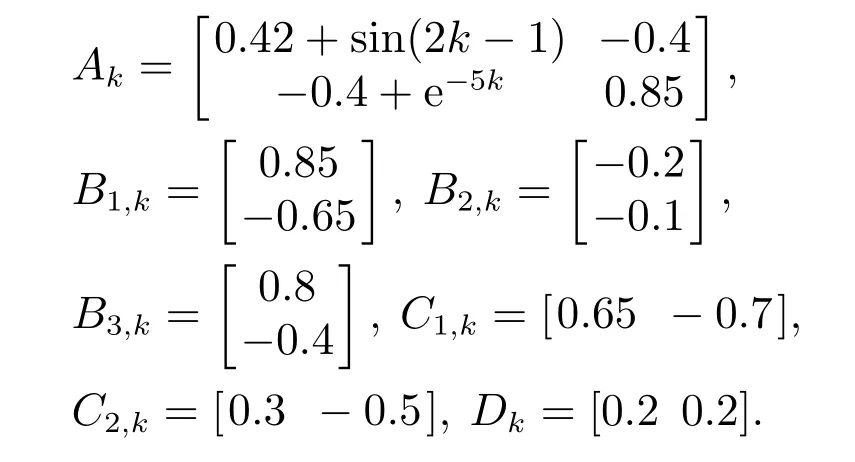
Let the FDI attack signals be

Case 1Assuming that the probability parameters are given asthe H∞attack attenuation levelγ=0.6,the positive definite matrixW=0.8I,the time horizonN=100,the performance weighting matricesQk=I,R1,k=1,R2,k=0.8 andR3,k=1,and the selected scalarhk=1.Using Algorithm 1,we can obtain the controller gain results as shown in Table 1.The controlled outputs of closed-loop system and open-loop system are shown in Fig.2,respectively,and the measured outputs under hybrid attacks and without attacks are shown in Fig.3,respectively.

Table 1 The controller gain results
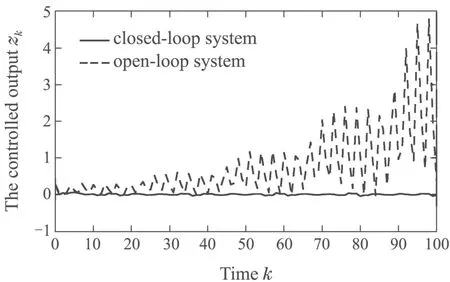
Fig.2 The controlled outputs of system

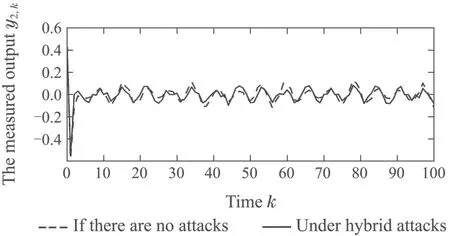
Fig.3 The measured outputs of system
Then we consider the case that the controller parametersKkare not optimal to minimize the linear quadratic performance functionJ2as we presented in Problem 2 and the other given conditions are the same as those given above,thus the controllers we obtained are common H∞performance controllers,which can be obtained by solving Problem 1.We can compare the results of permitted minimumγand the linear quadratic performance functionJ2in different cases,which are shown in Table 2,and the results comparison of controlled outputs are shown in Fig.4.

Table 2 The results comparison
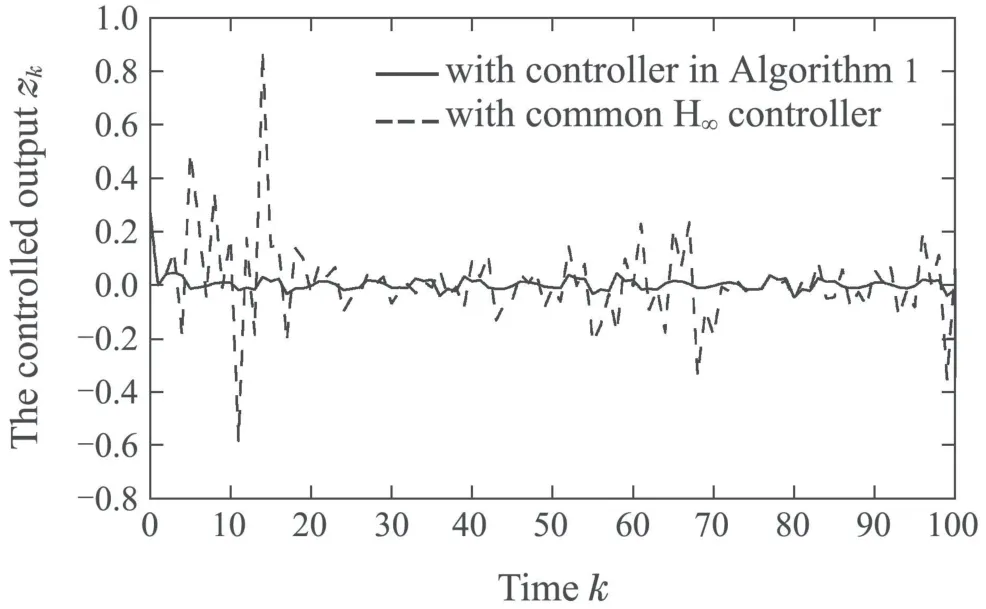
Fig.4 The controlled outputs with different algorithms
From the above numerical results and simulated figures,we can see that the controller design by Algorithm 1 is effective.
Case 2Assuming that the positive definite matrixW,the time horizonN,and the LQR performance weighting matrices are the same with them in Case 1.The probability parametercan change from 0.9 to 0.8,the scalarhkcan be selected as 1,1.1 and 1.2.The permitted minimumγresults are shown in Table 2.

Table 3 The permitted minimum γ
We can see from the above table that the permitted minimumγis related to the probability parameters and the scalarhk,that is to say,for the same scalarhk,if the probability parameters get smaller,it means that packet dropout probabilities get larger,then the permitted minimumγwill get larger;for the same packet dropout probabilities,if the scalarhkget larger,the permitted minimumγcould get larger or smaller.Then for the same packet dropout probabilities,we should select proper scalarhk,which can make the permitted minimumγget smaller.
5 Conclusions
This paper has presented the H∞performance control problem and given the design approach of controller for the security of time-varying CPS under hybrid attacks.The model of occurring two types of cyber attacks is presented,and the H∞performance requirement which represents the impact of attack signals on the controlled output in a finite-horizon is proposed.Based on the attack model and control objective,the suboptimal controller is designed to reduce the performance loss which the injected attack signals caused.Through theoretical research and simulation example,the approach we proposed can solve the control problem,reduce the performance loss,and increase security of CPS under hybrid attacks.
Appendix:

ProofBy defining then taking the mathematical expectation(A1),and applying the completing squares method results in


which means the pre-specified H∞performance requirement(5)is satisfied.The proof is complete. QED.
