Smart Body Sensor Object Networking
2014-07-19BhumipKhasnabish
Bhumip Khasnabish
(Strategy Planning and Standards Development,ZTE(TX)Inc.,USA)
Smart Body Sensor Object Networking
Bhumip Khasnabish
(Strategy Planning and Standards Development,ZTE(TX)Inc.,USA)
This paper discusses smart body sensor objects(BSOs),including their networking and internetworking.Smartness can be incorpo⁃rated into BSOs by embedding virtualization,predictive analytics,and proactive computing and communications capabilities.A few use cases including the relevant privacy and protocol requirements are also presented.General usage and deployment eti⁃quette along with the relevant regulatory implications are then discussed.
body sensor objects;body sensor networking object;virtualization;predictive analytics;body sensor usage etiquette
1 Introduction
This paper discusses the features,functions,and fea⁃sible implementation of smart body sensor objects (BSOs).Localized networking and relevant internet⁃working(using IP as glue)are also described for mobility and enterprise services[1].In[2]-[5],the major con⁃straints on implementing smart objects were memory,storage,bandwidth,code size,footprint(both size and weight),and en⁃ergy consumption and conservation.We propose incorporating smartness into wearable BSOs by embedding virtualization,predictive analytics,and proactive computing and communica⁃tion.Virtualization[6]-[10]of memory,storage and networking is prevalent in today’s computing and communication environ⁃ments,and it is only natural to extend virtualization into the emerging field of smart objects and networks.Prediction,such as Bayesian inference and associated analytics[1]-[10],is used to pre⁃position computing and communication facilities in addition to better managing network resources.Finally,proac⁃tive computing and communication enables efficient object pro⁃visioning and configuration management so that smart objects are deployed as smoothly as possible.A recent study revealed that the worldwide wearable computing market is growing,with almost 20 million shipments expected in 2014[11].
The rest of this paper is organized as follows.In section 2,we present a few use cases for BSOs.In section 2,we present a general BSO architecture.In section 4,we describe some im⁃plementations of BSOs.In section 5,we discuss smart BSO net⁃work(SBSON)models.In section 6,we discuss monitoring models based on body sensor network objects.In section 7,we give the results of experiments conducted on a BSO network. In section 8,we conclude the paper and discuss future work di⁃ rections.
2 Use Cases
2.1 Lifestyle Monitoring
Smart body sensors can be used to monitor lifestyle activi⁃ties,such as walking or jogging,yoga,swimming,talking,eat⁃ing,or other conventional or non⁃conventional body move⁃ments.It can also be used to monitor the triggers of allergic re⁃actions.Such monitoring should be followed by passive report⁃ing of the results(raw or correlated,in audio or text format)to pre⁃selected devices,which may include a device that a device worn by the person themselves.Sensors used for lifestyle moni⁃toring should be compact,comfortable,and non⁃intrusive.
2.2 Vital-Organ Monitoring
Smart body sensors can be used to monitor events and trig⁃gers related to vital organs.Such events and triggers can be monitored and reported at a regular(default)rate or a higher⁃than⁃normal rate.Triggers may be caused by abnormal activity in one organ,and this may affect the functioning of other or⁃gans.It is possible to develop templates for monitoring vital or⁃gans and events,and these templates can be used across differ⁃ent autonomous systems for rapid diagnosis and corrective mea⁃sures.As with lifestyle⁃monitoring sensors,monitoring should be followed by active or passive reporting of the raw or correlat⁃ed results.The objective is to stop the person’s vital organ from deteriorating while ambulance officers are on their way.It may be desirable that only sensors non⁃intrusive to others’per⁃sonal space be used for vital organ monitoring.If by mistake the sensors record any non⁃personal data or trigger,theseshould probably be treated as the property of a third party.
2.3 Black Box
A black box may be for private use(Pr.BB)or public use(Pu. BB).A Pr.BB can be used for smart⁃sensor monitoring and re⁃cording of heart and pulse rates,blood pressure,blood sugar levels,limb movements,speech,or even taking pictures of peo⁃ple you are talking to.A Pu.BB can be used for smart⁃sensor monitoring of what you are wearing,the street you are in,where you have come from,who you have met,and what you talked about and ate.This may also include watching the watcher,monitoring the potential perpetrator,analyzing and correlating events for taking proactive actions(passive or ac⁃tive step for protection),etc.There is a fine line between what is considered private and what is considered public,and laws and regulations may not be very clear in this area just yet.Fur⁃ther research is needed to provide local and universal guide⁃lines in this area.
3 Body Sensor Object
In general,a BSO comprises computing,communication,and service⁃specific sensors and application modules.Both computing and communication modules have generic and spe⁃cialized submodules.These submodules are special⁃purpose components and entities related to the services provided by the sensor.The submodules may be related to the sensing,monitor⁃ing,and analysis of temperature,images,graphics,pressure,vi⁃bration,or pollution.
The base Apps module of the BSO is concerned with data/ information collection,correlation,and decision⁃making(e.g.,comparison with a pre⁃set array of thresholds).This can be aug⁃mented by advanced or application⁃specific modules for gener⁃ating actionable,outlier⁃free intelligent data and alarms for lo⁃cal or remote use.Analytical and prediction capability can be extended by using virtualized computing and processing mod⁃ules according to the availability of resources.These capabili⁃ties reflect the smartness of the BSO.Appropriate lightweight application programming interfaces(APIs),such as HTTP pub⁃lish/subscribe model,are used for locating,accessing,reserv⁃ing,and using virtual communication port,logical channel,memory,processing,and storage.
The concept of BSO can be easily extended to cover body sensor network objects(BSNOs).The essential component of a BSNO is the networking module and component of the object. Bandwidth and security of the network channel are of para⁃mount importance in this scenario.As in[4],low⁃overhead pro⁃cessing and energy⁃efficient authorization,authentication,and encryption mechanisms must be used in constrained environ⁃ments such as a body sensor network.
Fig.1 shows high⁃level functional architecture of a BSNO. Fig.2 shows the modules for embedding smartness in a BSNO. Fig.3 and Fig.4a shows the virtualization of the entities of a BSO and BSNO through appropriate APIs.
Fig.4b shows personal data store(PDS)with collection,cat⁃egorization,storage,and APIs for providing appropriate ac⁃cess.Data can be collected from both private and public inter⁃actions of a person with applications and services,e.g.,email,web access and browsing;and system,e.g.,census and blogs. Maintenance,which includes archiving and categorization,can be based on different criteria.Access to the PDS may be for black box and other applications,and different APIs can be used after appropriate embedded or on⁃demand authentica⁃tion..Although further granularization is possible,at present,personal data can be categorized as private,public,secret,or top⁃secret(Fig.4b).
4 Body Sensor Implementation

Figure 1.▶High⁃level functional architecture of a smart body sensor network object.

▲Figure 2.Supplimentary body sensor network object modules for embedding smartness.

▲Figure 3.Virtualized entities in a body sensor object.

▲Figure 4.a)Virtualized entities in a body sensor network object,and b)architecture for personal data store.
A basic BSO contains the same computing and communica⁃ tion elements,but the sensing entities may depend on the tar⁃geted purpose.A radio frequency identifier(RFID)tag is also helpful and can be embedded into each of the body sensors.
When the basic elements are present,the rest of the entities can be implemented in different shapes and forms to fit the wearable device.For example,the shape of a wearable electro⁃cardiogram(ECG)sensor can be adjusted according to chest measurements(Fig.5).Similarly,a wearable pulse meter may contain a wristband and device that fits onto the finger tips (Fig.6).Fig.7 and Fig.8 shows Google Glass smart goggles that provide interfaces for recording and take snapshots of what one is seeing.It can also display stored,live,and on⁃de⁃mand video because antennas,speakers,and microphones are embedded in various parts of the goggles,such as the frame,bridge,and temples.Additional video monitoring and record⁃ing devices,e.g,a mini Bluetooth/Wi⁃Fi camera,can be in⁃stalled in the belt or collar(Fig.9).Various local mirco⁃USB,secure digital(SD),or cloud⁃based[3],[10]storage devices and wireless access points(WAPs)can be installed in the ear⁃muffs(Fig.10).Fig.11 shows a hard or soft hat⁃mountable de⁃vice,such as the WLAN,GPS,and LTE⁃capable Verizon Jet⁃ PackRby ZTE[12],as a WAP for direct com⁃munication with an Intranet,e.g.,body⁃area small cell or BASC,and as a gateway to the Internet for additional value⁃added BSNO services.
Devices that contain ECG sensors(Fig.5) and wearable pulse meters(Fig.6)are useful for lifestyle monitoring and vital⁃organ moni⁃toring.Smart goggles and camera⁃embedded belt or collar are integral components of both types of black box services discussed in sec⁃tion 2.Bluetooth and Wi⁃Fi⁃based peer⁃to⁃peer(session and transaction)services can be offered via the earmuffs(Fig.10)and/or hat⁃mounted virtual SSID capable WAP de⁃vices(Fig.11).Device ID login,service ID log in,and lightweight key⁃based encryption are required for session and transaction.Mes⁃sage Queuing Telemetry Transport(MQTT) [13]is gaining popularity as a lightweight publish/subscribe model for message trans⁃port between machines and smart objects. Some simple extensions to MQTT for smart BSNO services may be very useful.
5 Architecture of Network Containing Smart Body Sensor Network Objects
Our network contains lightweight User Da⁃tagram Protocol(UDP)over IP and Transmis⁃sion Control Protocol(TCP)over IP[1],[10]pipes,which lie over the underlying LTE,Wi⁃Fi,Bluetooth,and IEEE 802.15.4[1]-[10],[17]-[21]network.
Fig.12 shows a high⁃level architecture of such a network. Open server⁃side and open client⁃side APIs are used,and no specialized APIs are needed.Embedded web services using lightweight versions of protocols such as HTTP,XML,JSON,and Constrained Application Protocol(CoAP)[19]are used,de⁃pending on the footprint,power budget,and capability require⁃ments.Applications and services based on Vital⁃Organ Moni⁃toring Cluster(VMC)run seamlessly and have low memory and processing overhead.These applications and services are used for smart body sensor object networking.

▲Figure 5.Wearable ECG sensor with RFID tag(indicated by“R”)[14].

▲Figure 6.Wearable pulse meter with RFID tag[15].

▲Figure 7.Front⁃and⁃backside wearable smart goggles (e.g.,GoogleTMglass)with RFID tag.

▲Figure 8.Augmented realty goggles with RFID tag[16].

▲Figure 9.Miniature Bluetooth and Wi⁃Fi camera embedded into a belt or collar with RFID tag.

▲Figure 10.Storage(mUSB and SD for PBB)and WAP mountable earmuffs with RFID tags.

▲Figure 11.Hat⁃mountable Verizon JetPackR(by ZTE)with WLAN,GPS,and LTE.
Although there is a universal definition of vital organs,in some special cases,it may be necessary to identify the vital or⁃gan in context.For example,the lungs can be considered more vital to patients with breathing difficulties.
In addition to using an active RFID tag[1],[10],each BSO has another identifier for privacy and security reasons.Based on the pre⁃specified,pre⁃programmed interface,each BSO con⁃tinuously or periodically logs sensed data in a certain format,e. g.,comma⁃separated value(CSV)format.A BSO may also re⁃ceive input data from secondary and tertiary BSOs that may be members of the same BSO cluster group(via ClusterMaster or ClusterVisor(Fig.13).The stored log data is processed in real⁃time to locate anomalies,i.e.,threshold crossing and correlated events,and then uploaded to be archived or to replenish stored information.For example,a refined version of MQTT[13]can be used for automated local and remote status updating and generation of triggers(e.g.,alarm,call to ambulance).
Further analysis is done using clusters to discover abnormal⁃ities in the monitored information streams(Fig.14).

▲Figure 12.High⁃level architecture of a network that uses body sensor network objects.

▲Figure 13.Architecture for clustering and virtual⁃ring⁃based communication between smart body sensor objects.
Using the LTE uplink,information relating to anomaly and abnormality can be sent securely as top⁃secret information to remote databases.This top⁃secret information can be used by ambulance officers,specialists,and service providers for re⁃mote storage and appropriate preventative or corrective action.
6 Monitoring Models based on Body Sensor Network Objects
Depending on the state of the body organ being monitored,the state of a sensor may be idle(I)or active(A).In general,a simple two⁃state Markov chain model(Fig.15)can be used to model the monitoring state of a body sensor device.By solving the simple two⁃state model with appropriate simplifying as⁃sumptions,the probabilities of idle state PIand active state PA

Note thatpAIandpIAare the transition probabilities,from active to idle and from idle to active.Depending on the use case,the proba⁃bility of a sensor being active may be higher than the expected average of 50%.For exam⁃ple,during physical exercise,certain organs may need to be monitored more frequently in or⁃der to initiate preventative actions.Similarly,a sensor may remain idle for a long time depend⁃ing on the context and use case.
Fig.16 shows a more realistic three⁃state monitoring model.The additional state here is the monitor⁃worthy(MW)state,and the proba⁃bility of being in that state is given by PMW.The MW state can be considered a transitional state between idle and active.
By solving a three⁃state Markov chain model,we find that is given as


▲Figure 14.Steps for collecting and processing data collected by body sensors.

▲Figure 15.A simple two⁃state monitoring model based on body sensors.

▲Figure 16.A more realistic three⁃state monitoring model basedon body sensors.

The probability of transition from idle to MW is denoted pIM;the probability of transition from MW to active is denoted pMA;and the probability of transition from active to idle is d⁃enotedpAI.The probability that a sensor will be in any of three states is approximately 33%when the organ is function⁃ing normally(hence of the sensor).However,depending on the context,situation,and use case,a sensor may remain in MW state more often than in the idle state.
7 Results of Experiments on Body Sensor Network
In this section,we present the preliminary results from a simple experimental setup where only a limited number of sen⁃sors are utilized.The basic monitoring,computing,and commu⁃nications capability related features of the sensors along with some introductory results are presented in Tables 1-4 and Fig.17.
Data traffic appears in the cluster⁃master or cluster⁃visor

▼Table 1.ECG sensor’s features as SBSO

▼Table 2.Pulse meter’s features as SBSO

▼Table 3.Collar/belt⁃embedded camera features as SBSO
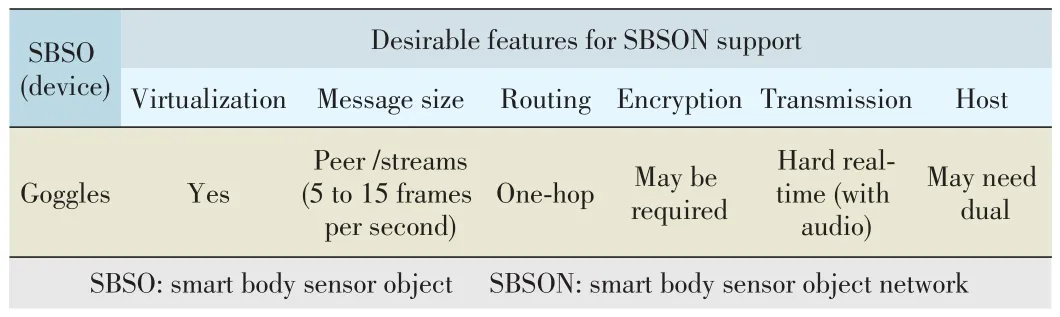
▼Table 4.Smart Goggle features as SBSO

▲Figure 17.Preliminary dealy variation and loss probability.
and virtual ring(Fig.12)in the pattern of micro⁃burst,peer⁃to⁃peer,or streams,depending on the type of monitoring de⁃scribed in Tables 1-4 and Fig.17.For rapid prototyping anddeveloping adaptive service⁃focused sensor apps,embedded LUA[22]can be used.The currently available eLUA modules [23]can be quickly customized and deployed in order to dy⁃namically satisfy the analytical,operational,and environmen⁃tal requirements.
Although no significant loss of monitoring data was observed using this simple setup,there was occasional variation in delay when the cluster⁃master or cluster⁃visor received monitored da⁃ta.This can be attributed to the switching of the mode of trans⁃mission from Bluetooth or PAN to VLAN or Wi⁃Fi,and vice⁃versa.It may be possible to overcome this by segmenting the network,assigning one mode to each segment for communica⁃tion to the cluster⁃master,or adding more cluster⁃masters to the ring.
The results in Fig.17a and 17b are based on 32 SBSOs in a 32 virtual⁃hop ring with two cluster⁃masters and two cluster⁃vi⁃sors.
We assume that:
•One in one thousand transmitted messages over a virtual hop(of the ring)can be corrupted or lost for various reasons (including mobility and interference).
•Cluster⁃master and cluster⁃visor has 32 MB or more of stor⁃age for each of the SBSOs in the ring for storing compressed and encrypted information.
•A message is considered obsolete(hence lost)once it has tra⁃versed 32 virtual hops(i.e.,traversed all of the nodes of the virtual ring but failed to reach the cluster⁃master/⁃visor.
The channels with different transmisison technologies trans⁃mit information in different directions over the virtual chan⁃nels,e.g.,PAN channels are configured to transmit information in clockwise direction over the ring,and Bluetooth channels transmit information in counetr⁃clock⁃wise direction).
8 Conclusion and Future Work
We have discussed SBSOs,including their networking and internetworking in the context of a set of use cases.These use cases are lifestyle monitoring,vital⁃organ monitoring,and col⁃lecting data and information for black box services.
To make sensors smart,we imbued them with virtualization,simple predictive analytics,and proactive computing and com⁃munication.We pointed out general usage and deployment eti⁃quette in Fig.4b and regulatory implications in the context of the use cases mentioned.[26]⁃[28]
We presented simple two⁃state and three⁃state models of monitoring by sensors as well as preliminary results from a sim⁃ple experimental setup where only a limited number of sensors were used.
We also discussed the use of virtualized ad⁃hoc networking using cluster⁃master or cluster⁃visor.
The following are future research directions that build on what we have presented here:
•Personalization of sensors.Probes and capabilities of sen⁃ sors can be personalized according to a person’s needs.
•Session⁃and transaction⁃specific authorization and authenti⁃cation of the sensors.This refers to the prevention of unau⁃thorized local or remote uploading of the monitored informa⁃tion for any session or transaction to or from the sensors.
•Self⁃destruct or beacon emitting sensors.This protects sen⁃sors against hacking or theft.A kill⁃switch can be embedded in the sensors in order to prevent any unauthorized use of lost or stolen sensors.
•Mechanisms to improve reliability,survivability,and sus⁃tainability of the sensor networks.This refers to the develop⁃ment and invocation of reliability⁃improving mechanisms in a virtualized environment for both body sensors and sensor network objects.
•Self⁃healing and self⁃monitoring smart sensors.This refers to developing implementable body sensors that have self⁃monitoring,self⁃calibrating,and self⁃healing components.
•Sensors powered by solar,body heator friction.This refers to developing low⁃power body sensors that can operate using a remote charger,solar power,body heat,or friction created by limbs or organs.A recent invention is a remote charger that powers wireless medical implants deep inside the body [24].
•Miniaturization of the SBSOs in order to embed them seam⁃lessly in body and everyday wearable garments.This refers to miniaturization of the body sensors so that these can be embedded in everyday wearable items like garments,shoes,ornaments,etc.A recent experiment utilized a miniature im⁃plantable device to treat heart failure patients with central sleep apnea[25].
•Mobile cloud[3]based operations and management of BSOs: This refers to seamless use of virtualization and automation for management,operation and orchestration of body sensor objects across multiple domains for mobile users.
[1]A.S.Esguevillas,B.Carro,B.Khasnabish,and A.Gupta,“Guest editorial:Ap⁃plications and support technologies for mobility and enterprise services,”IEEE Wireless Communications Magazine,vol.16,no.3,pp.6-7,Jun.2009.
[2]H.Tschofenig and J.Arkko.(2012,Apr.).Report from the smart object work⁃shop.[Online].Available:http://tools.ietf.org/rfc/rfc6574.txt
[3]B.Khasnabish.(2012 Sept.).Mobile cloud for personalized any⁃media services. ZTE Communications[Online].10(3),pp.47-54.Available:http://tinyurl.com/ bhumip⁃mobile⁃cloud
[4]J.Gilger and H.Tschofenig.(2012 Oct.).Smart object security workshop report. [Online].Available:http://tools.ietf.org/id/draft⁃gilger⁃smart⁃object⁃security⁃workshop⁃00.txt
[5]IETF.(2014).Light⁃Weight Implementation Guidance(LWIG)activities.[On⁃line].Available:http://datatracker.ietf.org/wg/lwig/charter
[6]IETF.(2014).Network Virtualization Overlays(NVO3)activities.[Online].Avail⁃able:http://datatracker.ietf.org/wg/nvo3/charter
[7]IETF.(2014).System for Cross⁃Domain Identity Management(SCIM)activities. [Online].Available:http://datatracker.ietf.org/wg/scim/charter
[8]IETF.(2014).Mobile Ad⁃hoc Networks(MANET)activities.[Online].Available: http://datatracker.ietf.org/wg/manet/charter
[9]IRTF.(2014).Software Defined Networking Research Group(SDN⁃RG)activi⁃ties.[Online].Available:https://irtf.org/sdnrg
[10]T.Plevyak and V.Sahin,Neχt Generation Telecommunications Networks,Servic⁃es,and Management.New Jersey:Wiley⁃IEEE Press Book,Apr.2010.
[11]C114.(2014 Apr.).Worldwide wearable computing device shipment prediction.[Online].Available:http://www.cn⁃c114.net/583/a830917.html
[12]ZTE Corporation.(2014).Verizon JetPackR890L.[Online].Available:http:// www.zteusa.com/verizon⁃jetpacktm⁃890l.html
[13]MQTT.(2014).Message Queuing Telemetry Transport(MQTT)for lightweight publish/subscribe messaging transport.[Online].Available:http://mqtt.org/
[14]NICT.(2014).Wearable ECG sensor image.[Online].Available:http://www. nict.go.jp
[15]Clinical Guard.(2014).Wearable pulse meter image.[Online].Available:http:// www.clinicalguard.com
[16]Recon Instruments.(2013).Augmented reality Goggle image.[Online].Avail⁃able:http://www.reconinstruments.com
[17]IETF.(2014).IPv6 over Low Power WPAN(6LOWPAN)activities.[Online]. Available:http://datatracker.ietf.org/wg/6lowpan/charter
[18]IETF.(2014).Routing Over Low Power and Lossy Networks(ROLL)activities. [Online].Available:http://datatracker.ietf.org/wg/roll/charter
[19]IETF.(2014).Constrained RESTful Environments(CORE)activities.[Online]. Available:http://datatracker.ietf.org/wg/core/charter
[20]IETF.(2014).Transport Layer Security(TLS)activities.[Online].Available: http://datatracker.ietf.org/wg/tls/charter
[21]IEEE.(2014).802.15 WPAN™Task Group 4(TG4).[Online].Available:http:// www.ieee802.org/15/pub/TG4.html
[22]eLua.(2014).Service⁃focused sensor apps using Embedded LUA(eLUA).[On⁃line].Available:http://www.eluaproject.net
[23]eLua.(2014).Service⁃focused Embedded LUA(eLUA)modules.[Online]. Available:http://www.eluaproject.net/overview/status
[24]MNT.(2014,May 21).Invention powers wireless medical implants deep inside the body.[Online].Available:http://www.medicalnewstoday.com/articles/ 277110.php
[25]MNT.(2014,May 20).Implantable device treats heart failure patients with cen⁃tral sleep apnea.[Online].Available:http://www.medicalnewstoday.com/arti⁃ cles/277032.php
[26]IEEE.(2014 May).Body Sensor Networks(BSN)Conf.[Online].Available:http: //www.bsn2012.org
[27]IEEE.(2013 May).Body Sensor Networks(BSN)Conf.[Online].Available:http: //toc.proceedings.com/19075webtoc.pdf
[28]IEEE.(2014 Jun.).Body Sensor Networks(BSN)Conf.[Online].Available:http: //www.bsn2014.org
Biographyraphy
Bhumip Khasnabish(bhumip.khasnabish@ztetx.com),PhD,is a senior member of the IEEE and an emeritus distinguished lecturer of the IEEE Communications Soci⁃ety.He initiated cloud and data center activities in IETF and is vice⁃chair of DMTF NSM WG.He previously co⁃chaired the ATIS IPTV Interoperability Forum(IIF) and founded and chaired ATIS NG⁃CI TF and MSF Services WG.He is currently se⁃nior director in the Strategy Planning and Standards Development Department,ZTE USA.His research interests include next⁃generation networking;platform and ser⁃vices that use virtualized computing,communication,and service entities;tighter cross⁃layer communications;software⁃defined networking;and system configuration/ service automation.
Dr.Khasnabish has authored numerous articles,book chapters,books,and pat⁃ents in areas related to converged services and next⁃generation networking.His lat⁃est book,Implementing Voice over IP(Wiley⁃IEEE Press,2003)is currently in its second printing.Dr.Khasnabish has co⁃edited Multimedia Communications Net⁃works:Technologies and Services(Artech House,1998)and many special issues of IEEE Network,IEEE Wireless Communications,IEEE Communications,and the Journal of Network and Systems Management.
Smartphones to Account for 2/3 of World’s Mobile Market by 2020, Says New GSMA Intelligence Study
11 September 2014,Hong Kong:Smartphones will ac⁃count for two out of every three mobile connections global⁃ly by 2020,according to a major new report by GSMA In⁃telligence,the research arm of the GSMA.The new study,“Smartphone forecasts and assumptions,2007-2020”,finds that smartphones account for one in three mobile con⁃nections today,representing more than two billion mobile connections.It forecasts that the number of smartphone connections will grow three⁃fold over the next six years,reaching six billion by 2020,accounting for two⁃thirds of the nine billion mobile connections by that time.Basic phones,feature phones and data terminals will account for the remaining connections.The study excludes M2M from the connections totals.
“The smartphone has sparked a wave of global innova⁃tion that has brought new services to millions and efficien⁃cies to businesses of every type,”said Hyunmi Yang,Chief Strategy Officer at the GSMA.“As the study re⁃leased today shows,smartphones will be the driving force of mobile industry growth over the next six years,with one billion new smartphone connections expected over the next 18 months alone.
The developing world overtook the developed world in terms of smartphone connections in 2011 and today ac⁃counts for two in every three smartphones on the planet,ac⁃cording to the new study.It is predicted that by 2020,four out of every five smartphone connections worldwide will come from the developing world.
Asia Pacific today accounts for about half of global smartphone connections,even though smartphone penetra⁃tion in the region is currently calculated at below 40 per cent.The Asia Pacific total is boosted by the inclusion of China,the world’s largest smartphone market,with more than 629 million smartphone connections.
In many developed markets,smartphone penetration is approaching the 70 to 80 per cent“ceiling”at which growth tends to slow.According to the report,smartphone adoption is forecast to reach 75 per cent in Europe and North America by 2020.Smartphone growth in these two regions has slowed in recent years;smartphone connec⁃tions grew by 35 per cent in North America and by 39 per cent in Europe between 2010 and 2013,compared to growth rates of over 80 per cent during the period in Asia Pacific and Latin America.(Source:c114)
t
2014-03-24
10.3969/j.issn.1673-5188.2014.03.005
http://www.cnki.net/kcms/detail/34.1294.TN.20140903.1443.002.html,published online 3 September,2014
杂志排行
ZTE Communications的其它文章
- Reliability of NFV NFV Using COTS Hardware
- MAC Layer Resource Allocation for Wireless Body Area Networks
- Prototype for Integrating Internet of Things and Emergency Service in an IP Multimedia Subsystem for Wireless Body Area Networks
- Wireless Body Area Networks for Pervasive Healthcare and Smart Environments
- Selective Cluster⁃Based Temperature Monitoring System for Homogeneous Wireless Sensor Networks
- E-Healthcare Supported by Big Data
